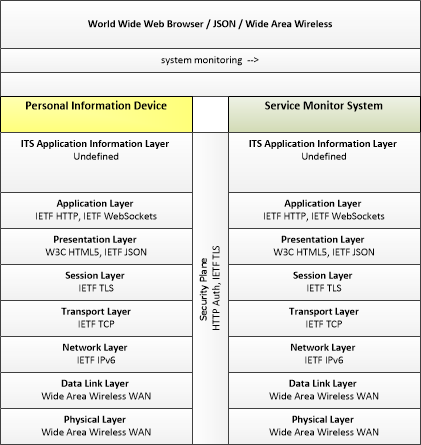
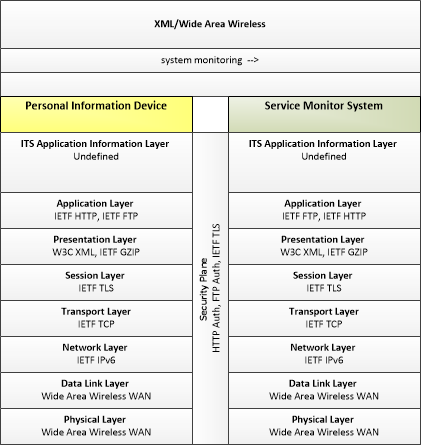
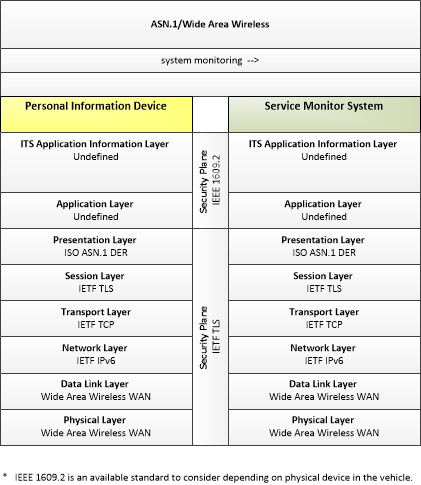
Link Type: Wide-Area Wireless
Personal Information Device --> Service Monitor System:
system monitoring
Definitions
system monitoring (Information Flow): Represents the interactive monitoring of system operations by the Service Monitor. It includes device housekeeping/heartbeat monitoring and network monitoring information, the status of installed applications, and the configuration of managed devices.
Personal Information Device (Source Physical Object): The 'Personal Information Device' provides the capability for travelers to receive formatted traveler information wherever they are. Capabilities include traveler information, trip planning, and route guidance. Frequently a smart phone, the Personal Information Device provides travelers with the capability to receive route planning and other personally focused transportation services from the infrastructure in the field, at home, at work, or while en-route. Personal Information Devices may operate independently or may be linked with connected vehicle on-board equipment.
Service Monitor System (Destination Physical Object): The 'Service Monitor System' represents one or more center-based systems that provide monitoring, management and control services necessary to other applications and/or devices operating within the Connected Vehicle Environment. These support services enable other applications to provide transportation services.
Included In
This Information Flow is in the following Applications:
This Information Flow is in the following Application Objects:
Communication Diagrams
The communication diagram(s) can be viewed in SVG or PNG format and the current format is SVG. Switch to PNG format.
This profile describes applicable XML and W3C web services standards used in transmissions over wide area wireless communications.
This profile describes applicable ASN.1 standards used in transmissions over wide area wireless communications.
Characteristics
Architectural:
| Characteristic | Value |
|---|---|
| Time Context | Recent |
| Spatial Context | Adjacent |
| Acknowledgement | True |
| Cardinality | Unicast |
| Initiator | Destination |
Security
This information flow triple is in the following applications with the following security levels.
| Information Flow Security | |||||
|---|---|---|---|---|---|
| Application | Confidentiality | Integrity | Availability | ||
| Basis | Basis | Basis | |||
| Security levels have not been defined yet. | |||||