Link Type: Contact or Proximity
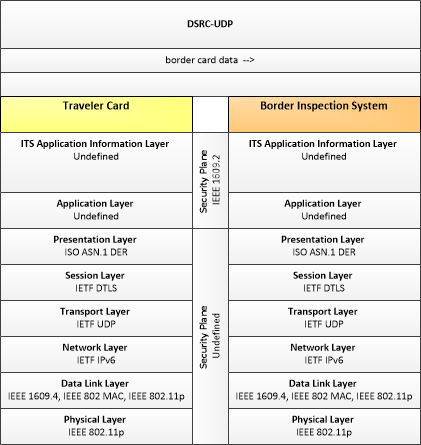
Traveler Card --> Border Inspection System:
border card data
Definitions
border card data (Information Flow): Personal identification data from ID cards used by travelers at border crossings.
Traveler Card (Source Physical Object): The 'Traveler Card' stores traveler identification information, including biometric information, that can be used in trusted traveler programs to expedite clearance through security checkpoints at borders or security-critical areas.
Border Inspection System (Destination Physical Object): 'Border Inspection System' represents data systems used at the border for the inspection of people or goods. It supports immigration, customs (trade), agricultural, and FDA inspections as applicable. It includes sensors and surveillance systems to identify and classify drivers and their cargo as they approach a border crossing, the systems used to interface with the back-office administration systems and provide information on status of the crossing or events.
Included In
This Information Flow is in the following Applications:
This Information Flow is in the following Application Objects:
Communication Diagrams
The communication diagram(s) can be viewed in SVG or PNG format and the current format is SVG. Switch to PNG format.
Characteristics
Architectural:
| Characteristic | Value |
|---|---|
| Time Context | Recent |
| Spatial Context | Adjacent |
| Acknowledgement | False |
| Cardinality | Unicast |
| Initiator | Source |
Security
This information flow triple is in the following applications with the following security levels.
| Information Flow Security | |||||
|---|---|---|---|---|---|
| Application | Confidentiality | Integrity | Availability | ||
| Basis | Basis | Basis | |||
| Border Management Systems | High | Moderate | High | ||
| This data contains all of the information needed to identify a traveler. If a criminal was able to view this data, it could be used to impersonate the traveler. | The identity reported by this transmission might not actually be the individual in the vehicle. As such there is no way that this could have HIGH integrity, and is why other sources must be used to ensure that this individual is who they are claiming to be. | If the traveler card data was not delivered to the RSE by Vehicle OBE this will be the last chance for the card to be validated. If it fails, the traveler will likely be turned away from the border and not be allowed to cross. This would be equivalent to arriving at the border today without a passport, however it would be the system's fault, not the user's. Since there is no alternate way for an individual to prove their identity, this could break the whole system and should not happen. | |||