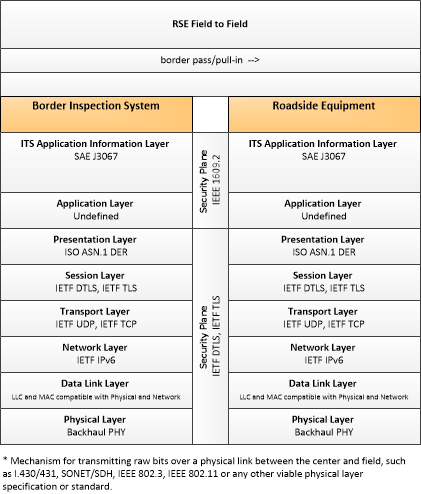
Link Type: Field to Field
Border Inspection System --> Roadside Equipment:
border pass/pull-in
Definitions
border pass/pull-in (Information Flow): Command to commercial vehicle to pull into or bypass border inspection station
Border Inspection System (Source Physical Object): 'Border Inspection System' represents data systems used at the border for the inspection of people or goods. It supports immigration, customs (trade), agricultural, and FDA inspections as applicable. It includes sensors and surveillance systems to identify and classify drivers and their cargo as they approach a border crossing, the systems used to interface with the back-office administration systems and provide information on status of the crossing or events.
Roadside Equipment (Destination Physical Object): 'Roadside Equipment' (RSE) represents the Connected Vehicle roadside devices that are used to send messages to, and receive messages from, nearby vehicles using Dedicated Short Range Communications (DSRC) or other alternative wireless communications technologies. Communications with adjacent field equipment and back office centers that monitor and control the RSE are also supported. This device operates from a fixed position and may be permanently deployed or a portable device that is located temporarily in the vicinity of a traffic incident, road construction, or a special event. It includes a processor, data storage, and communications capabilities that support secure communications with passing vehicles, other field equipment, and centers.
Included In
This Information Flow is in the following Applications:
This Information Flow is in the following Application Objects:
Communication Diagrams
The communication diagram(s) can be viewed in SVG or PNG format and the current format is SVG. Switch to PNG format.
Characteristics
Architectural:
| Characteristic | Value |
|---|---|
| Time Context | Recent |
| Spatial Context | Adjacent |
| Acknowledgement | True |
| Cardinality | Unicast |
| Initiator | Source |
Security
This information flow triple is in the following applications with the following security levels.
| Information Flow Security | |||||
|---|---|---|---|---|---|
| Application | Confidentiality | Integrity | Availability | ||
| Basis | Basis | Basis | |||
| Border Management Systems | Not Applicable | High | Moderate | ||
| This is directly observable data. | This message is directly acted upon. It should not be possible to spoof a border inspection station bypass. | The system should know if these messages are not received. If the messages are not received, the system should fail safely, with the border agents performing additional inspections. | |||