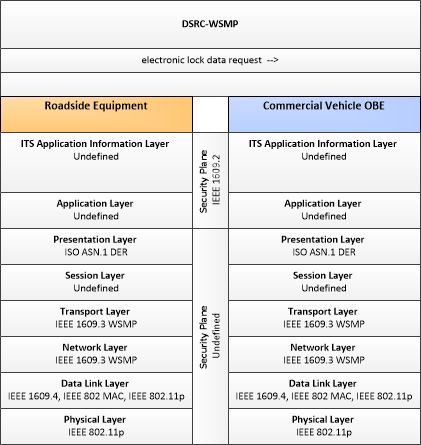
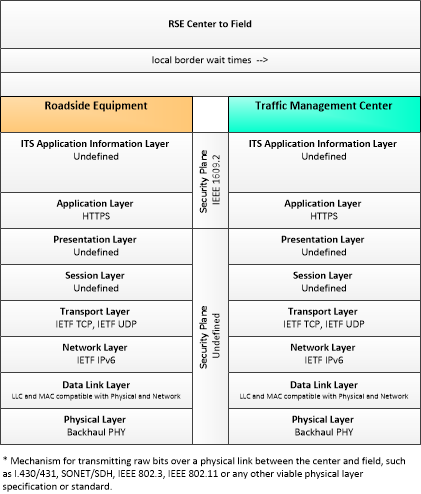
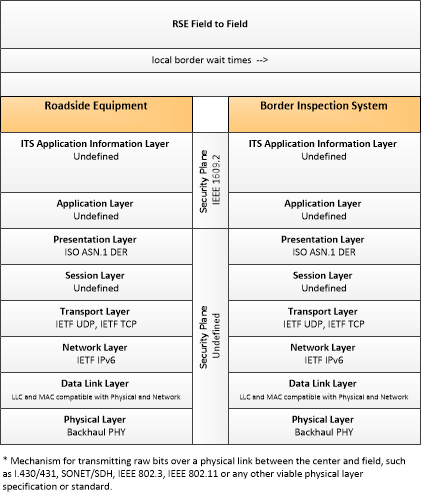
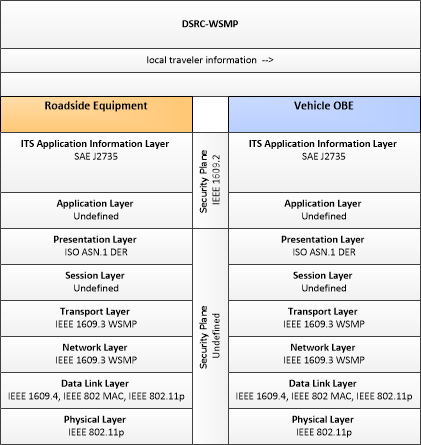
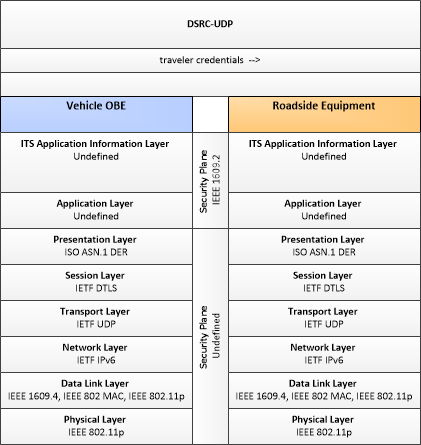
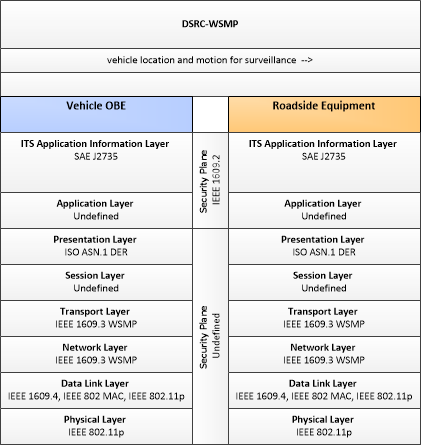
Type: Mobility
Groups:- Border
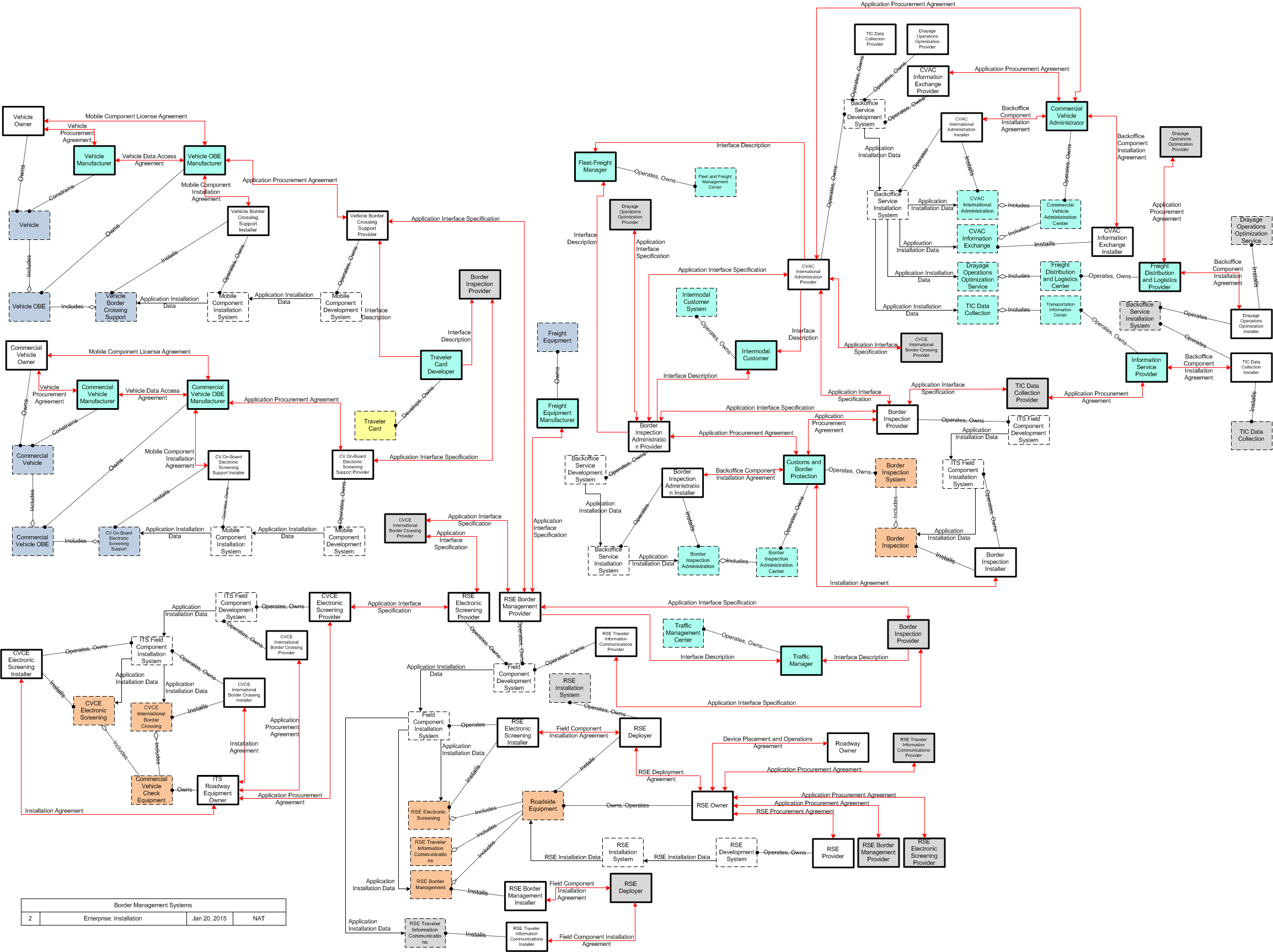
Border Management Systems
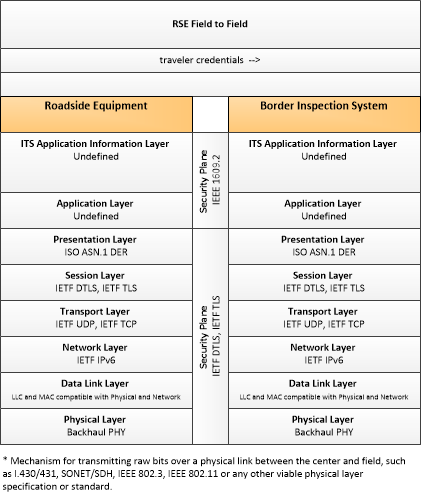
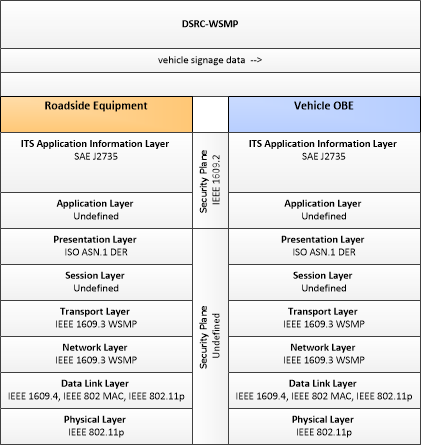
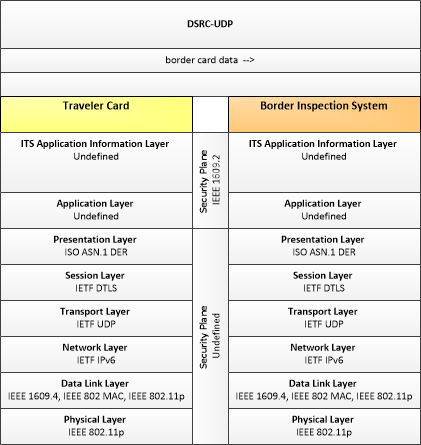
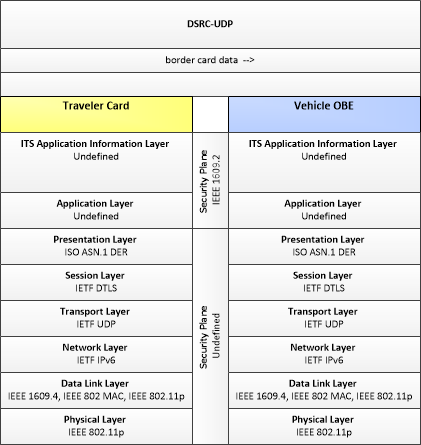
Border Management Systems applications provide international border registration, pre-processing and border inspection capabilities. The registration and pre-processing cover electronic interactions between the border agencies and the fleet management agencies. The border inspection capabilities include electronic communications between the commercial vehicles, freight containers, and border inspection services.
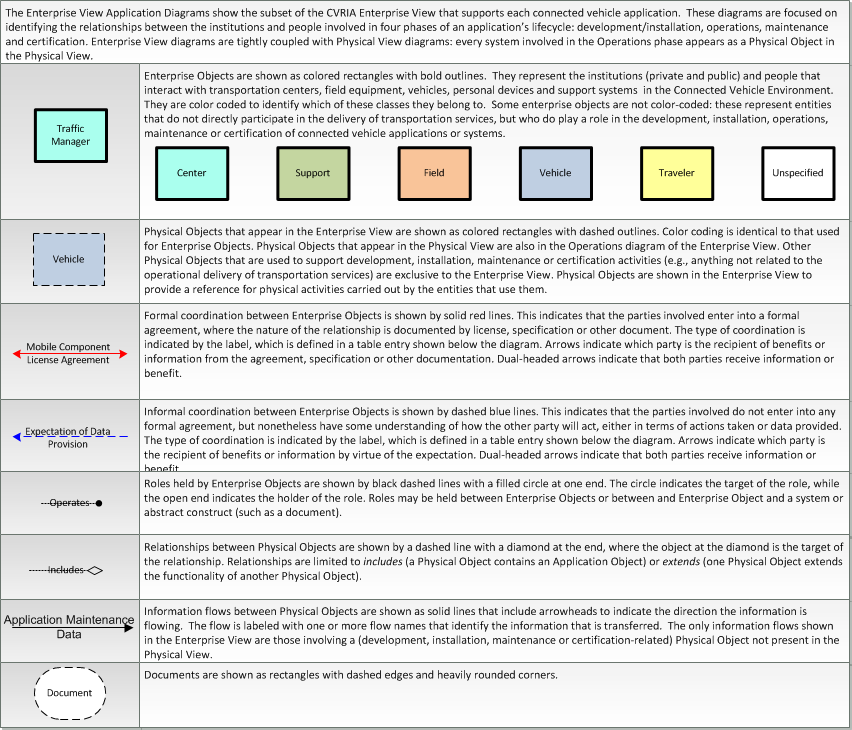
Enterprise
This is one way this application may be realized, but not the only way. There are other ways to build a given application and accomplish a stated objective.
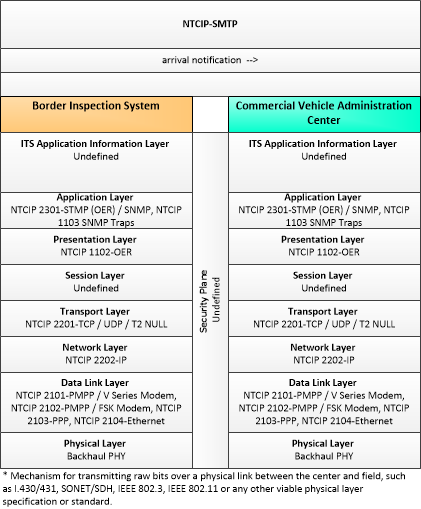
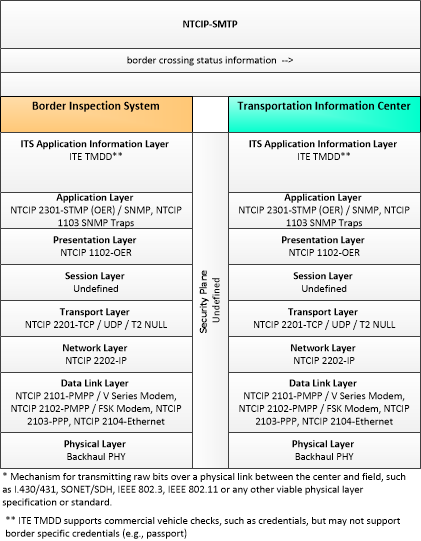
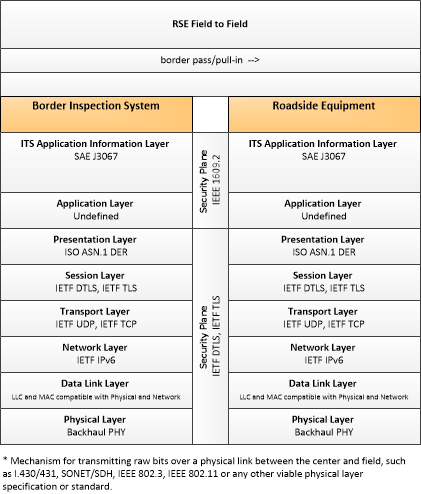
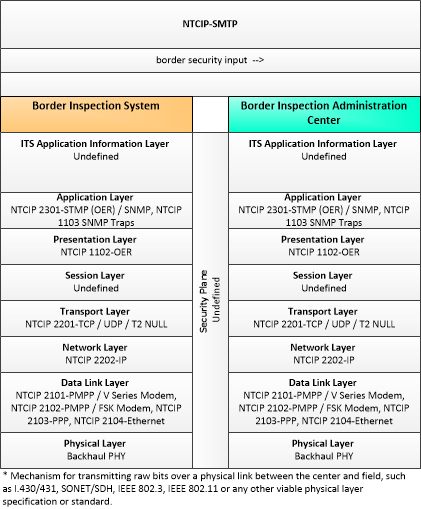
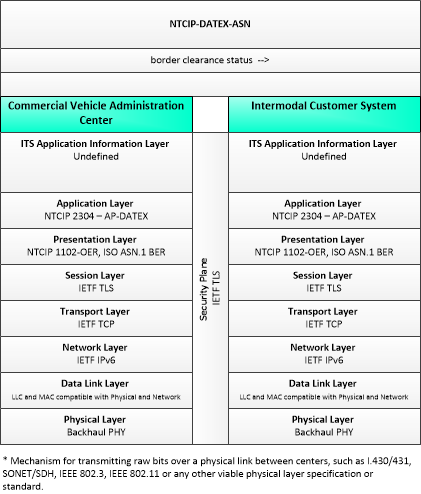
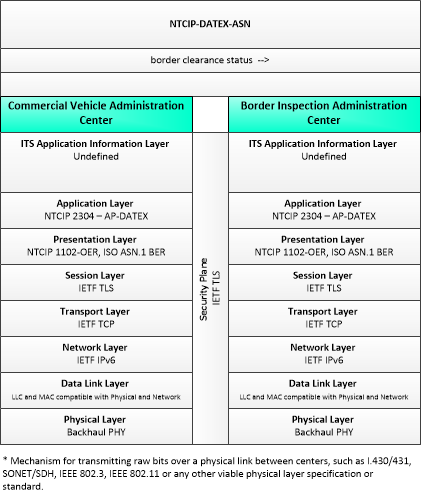
The enterprise diagram can be viewed in SVG or PNG format and the current format is SVG. SVG Diagrams: Installation Operations Maintenance Certification
PNG Diagrams: Installation Operations Maintenance Certification
Business Interaction Matrix:
| Border Management Systems Operations Stage | |||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Vehicle Owner | Driver | Vehicle OBE Owner | Roadway Owner | RSE Owner | RSE Operator | ITS Roadway Equipment Owner | ITS Roadway Operator | Fleet-Freight Manager | Freight Distribution and Logistics Provider | Commercial Vehicle Owner | Freight Equipment Owner | Commercial Vehicle Driver | Intermodal Customer | Traffic Manager | Information Service Provider | RSE Traveler Information Communications Provider | Traveler | Commercial Vehicle Administrator | Customs and Border Protection | RSE Electronic Screening Provider | CV On-Board Electronic Screening Support Provider | Freight Equipment Monitoring Provider | RSE Border Management Provider | Vehicle Border Crossing Support Provider | |
| Vehicle Owner | Vehicle Usage Agreement | Vehicle OBE Usage Agreement | Application Usage Agreement | ||||||||||||||||||||||
| Driver | Vehicle Usage Agreement | ||||||||||||||||||||||||
| Vehicle OBE Owner | Vehicle OBE Usage Agreement | Expectation of Information Provision | Expectation of Information Provision | ||||||||||||||||||||||
| Roadway Owner | Service Delivery Agreement | ||||||||||||||||||||||||
| RSE Owner | Expectation of Information Provision | Service Delivery Agreement | Operations Agreement | Information Exchange and Action Agreement | Expectation of Information Provision | Expectation of Information Provision | Information Provision Agreement | Application Usage Agreement | Information Exchange Agreement | Application Usage Agreement | Application Usage Agreement | ||||||||||||||
| RSE Operator | Operations Agreement | ||||||||||||||||||||||||
| ITS Roadway Equipment Owner | Information Exchange and Action Agreement | Operations Agreement | Information Exchange and Action Agreement | Expectation of Information Provision | |||||||||||||||||||||
| ITS Roadway Operator | Operations Agreement | ||||||||||||||||||||||||
| Fleet-Freight Manager | Expectation of Information Provision | Expectation of Information Provision | |||||||||||||||||||||||
| Freight Distribution and Logistics Provider | Expectation of Information Provision | ||||||||||||||||||||||||
| Commercial Vehicle Owner | Expectation of Information Provision | Vehicle Operating Agreement | Application Usage Agreement | ||||||||||||||||||||||
| Freight Equipment Owner | Expectation of Information Provision | Application Usage Agreement | |||||||||||||||||||||||
| Commercial Vehicle Driver | Vehicle Operating Agreement | ||||||||||||||||||||||||
| Intermodal Customer | Expectation of Information Provision | Expectation of Information Provision | |||||||||||||||||||||||
| Traffic Manager | Information Provision Agreement | Information Provision Agreement | |||||||||||||||||||||||
| Information Service Provider | Information Provision Agreement | ||||||||||||||||||||||||
| RSE Traveler Information Communications Provider | Application Usage Agreement | ||||||||||||||||||||||||
| Traveler | Expectation of Information Provision | Expectation of Data Provision | |||||||||||||||||||||||
| Commercial Vehicle Administrator | Information Exchange and Action Agreement | Expectation of Information Provision | Expectation of Information Provision | Information Exchange and Action Agreement | |||||||||||||||||||||
| Customs and Border Protection | Information Exchange Agreement | Expectation of Information Provision | Expectation of Information Provision | Expectation of Information Provision | Expectation of Information Provision | Information Provision Agreement | Information Provision Agreement | Expectation of Data Provision | Information Exchange and Action Agreement | ||||||||||||||||
| RSE Electronic Screening Provider | Application Usage Agreement | ||||||||||||||||||||||||
| CV On-Board Electronic Screening Support Provider | Application Usage Agreement | ||||||||||||||||||||||||
| Freight Equipment Monitoring Provider | Application Usage Agreement | ||||||||||||||||||||||||
| RSE Border Management Provider | Application Usage Agreement | ||||||||||||||||||||||||
| Vehicle Border Crossing Support Provider | Application Usage Agreement | ||||||||||||||||||||||||
Includes Enterprise Objects:
| Enterprise Object | Description |
|---|---|
| Application Certification Entity | The body that determines whether an application may be deployed and operated in the Connected Vehicle Environment. This entity's composition, the requirements it applies and the procedures it uses to verify those requirements may vary with application type. For example, applications with human safety component (crash avoidance, movement assistance etc.) may have stringent requirements and extensive testing in a variety of conditions, while applications that provide strictly mobility functionality may have far less testing requirements; possibly as little as just making sure the application doesn't interfere with any other applications. |
| Border Inspection Administration Installer | Application Component Installers are specified more by role than by function. Installers are responsible for the installation of the application component, which may require a support system, and may entail agreements and relationships between end users and application providers. |
| Border Inspection Administration Maintainer | Application Component Maintainers are specified more by role than by function. Maintainers are responsible for the maintenance (configuration changes, patches and updates, hardware repairs) of the application component, which may require a support system, and may entail agreements and relationships between end users and application providers. |
| Border Inspection Administration Provider | Application Component Providers are specified more by role than by function. Providers are responsible for the development of the application component, including initial creation, enhancement and bug fixes. Delivery of the application to the end user may require relationships with other entities (installers, maintainers) if the provider chooses not to fulfill those roles. |
| Border Inspection Installer | Application Component Installers are specified more by role than by function. Installers are responsible for the installation of the application component, which may require a support system, and may entail agreements and relationships between end users and application providers. |
| Border Inspection Maintainer | Application Component Maintainers are specified more by role than by function. Maintainers are responsible for the maintenance (configuration changes, patches and updates, hardware repairs) of the application component, which may require a support system, and may entail agreements and relationships between end users and application providers. |
| Border Inspection Provider | Application Component Providers are specified more by role than by function. Providers are responsible for the development of the application component, including initial creation, enhancement and bug fixes. Delivery of the application to the end user may require relationships with other entities (installers, maintainers) if the provider chooses not to fulfill those roles. |
| Commercial Vehicle Administrator | The organization responsible for the administration functions performed by the Commercial Vehicle Administration Center. |
| Commercial Vehicle Driver | The 'Commercial Vehicle Driver' represents the people that operate vehicles transporting goods, including both long haul trucks and local pick-up and delivery vans. This physical object is complementary to the Driver physical object in that it represents those interactions which are unique to Commercial Vehicle Operations. Information flowing from the Commercial Vehicle Driver includes those system inputs specific to Commercial Vehicle Operations. |
| Commercial Vehicle Manufacturer | The entity which builds commercial vehicles, including long haul trucks and local pick up and delivery vehicles. This entity is complementary to the Vehicle Manufacturer entity in that it represents those aspects of vehicle manufacture which are unique to commercial vehicles. |
| Commercial Vehicle OBE Manufacturer | The Commercial Vehicle OBE Manufacturer is the provider of the commercial vehicle on-board equipment. This entity may design and build the OBE, or may integrate other components to form the OBE, or may use some combination of approaches to provide the on-board equipment. Since the OBE could be aftermarket, retrofit, built-in or nomadic, this entity is the one that builds whatever that-is. In some cases it may be a smart phone manufacturer, or in others a top tier parts supplier, or any other entity in the production chain, depending on the device and commercial vehicle in question. |
| Commercial Vehicle Owner | The entity that owns the commercial vehicle. This entity is complementary to the Vehicle Owner in that it represents those aspects of ownership which are unique to commercial vehicles. |
| Customs and Border Protection | The Department of Homeland Security's Customs and Border Protection |
| CV On-Board Electronic Screening Support Installer | Application Component Installers are specified more by role than by function. Installers are responsible for the installation of the application component, which may require a support system, and may entail agreements and relationships between end users and application providers. |
| CV On-Board Electronic Screening Support Maintainer | Application Component Maintainers are specified more by role than by function. Maintainers are responsible for the maintenance (configuration changes, patches and updates, hardware repairs) of the application component, which may require a support system, and may entail agreements and relationships between end users and application providers. |
| CV On-Board Electronic Screening Support Provider | Application Component Providers are specified more by role than by function. Providers are responsible for the development of the application component, including initial creation, enhancement and bug fixes. Delivery of the application to the end user may require relationships with other entities (installers, maintainers) if the provider chooses not to fulfill those roles. |
| CVAC Information Exchange Installer | Application Component Installers are specified more by role than by function. Installers are responsible for the installation of the application component, which may require a support system, and may entail agreements and relationships between end users and application providers. |
| CVAC Information Exchange Maintainer | Application Component Maintainers are specified more by role than by function. Maintainers are responsible for the maintenance (configuration changes, patches and updates, hardware repairs) of the application component, which may require a support system, and may entail agreements and relationships between end users and application providers. |
| CVAC Information Exchange Provider | Application Component Providers are specified more by role than by function. Providers are responsible for the development of the application component, including initial creation, enhancement and bug fixes. Delivery of the application to the end user may require relationships with other entities (installers, maintainers) if the provider chooses not to fulfill those roles. |
| CVAC International Administration Installer | Application Component Installers are specified more by role than by function. Installers are responsible for the installation of the application component, which may require a support system, and may entail agreements and relationships between end users and application providers. |
| CVAC International Administration Maintainer | Application Component Maintainers are specified more by role than by function. Maintainers are responsible for the maintenance (configuration changes, patches and updates, hardware repairs) of the application component, which may require a support system, and may entail agreements and relationships between end users and application providers. |
| CVAC International Administration Provider | Application Component Providers are specified more by role than by function. Providers are responsible for the development of the application component, including initial creation, enhancement and bug fixes. Delivery of the application to the end user may require relationships with other entities (installers, maintainers) if the provider chooses not to fulfill those roles. |
| CVCE Electronic Screening Installer | Application Component Installers are specified more by role than by function. Installers are responsible for the installation of the application component, which may require a support system, and may entail agreements and relationships between end users and application providers. |
| CVCE Electronic Screening Maintainer | Application Component Maintainers are specified more by role than by function. Maintainers are responsible for the maintenance (configuration changes, patches and updates, hardware repairs) of the application component, which may require a support system, and may entail agreements and relationships between end users and application providers. |
| CVCE Electronic Screening Provider | Application Component Providers are specified more by role than by function. Providers are responsible for the development of the application component, including initial creation, enhancement and bug fixes. Delivery of the application to the end user may require relationships with other entities (installers, maintainers) if the provider chooses not to fulfill those roles. |
| CVCE International Border Crossing Installer | Application Component Installers are specified more by role than by function. Installers are responsible for the installation of the application component, which may require a support system, and may entail agreements and relationships between end users and application providers. |
| CVCE International Border Crossing Maintainer | Application Component Maintainers are specified more by role than by function. Maintainers are responsible for the maintenance (configuration changes, patches and updates, hardware repairs) of the application component, which may require a support system, and may entail agreements and relationships between end users and application providers. |
| CVCE International Border Crossing Provider | Application Component Providers are specified more by role than by function. Providers are responsible for the development of the application component, including initial creation, enhancement and bug fixes. Delivery of the application to the end user may require relationships with other entities (installers, maintainers) if the provider chooses not to fulfill those roles. |
| Device Certification Entity | The body that determines whether a device may be deployed and operated in the Connected Vehicle Environment. This entity's composition, the requirements it applies and the procedures it uses to verify those requirements may vary with device type. |
| Drayage Operations Optimization Installer | Application Component Installers are specified more by role than by function. Installers are responsible for the installation of the application component, which may require a support system, and may entail agreements and relationships between end users and application providers. |
| Drayage Operations Optimization Maintainer | Application Component Maintainers are specified more by role than by function. Maintainers are responsible for the maintenance (configuration changes, patches and updates, hardware repairs) of the application component, which may require a support system, and may entail agreements and relationships between end users and application providers. |
| Drayage Operations Optimization Provider | Application Component Providers are specified more by role than by function. Providers are responsible for the development of the application component, including initial creation, enhancement and bug fixes. Delivery of the application to the end user may require relationships with other entities (installers, maintainers) if the provider chooses not to fulfill those roles. |
| Driver | The 'Driver' represents the person that operates a vehicle on the roadway. Included are operators of private, transit, commercial, and emergency vehicles where the interactions are not particular to the type of vehicle (e.g., interactions supporting vehicle safety applications). The Driver originates driver requests and receives driver information that reflects the interactions which might be useful to all drivers, regardless of vehicle classification. Information and interactions which are unique to drivers of a specific vehicle type (e.g., fleet interactions with transit, commercial, or emergency vehicle drivers) are covered by separate objects. |
| Federal Regulatory | Federal regulatory bodies that have legal authority to control and/or provide input to policies regulating transportation infrastructure and operations. This includes entities such as the Federal Communications Commission and US Department of Transportation. |
| Fleet-Freight Manager | The 'Fleet-Freight Manager' represents the people that are responsible for the dispatching and management of Commercial Vehicle fleets (e.g. traditional Fleet Managers) and Freight Equipment assets. It may be many people in a large tracking organization or a single person (owner driver) in the case of single vehicle fleets. The Fleet-Freight Manager provides instructions and coordination for Commercial Vehicles and Freight Equipment and receives the status of the vehicles and freight equipment in the fleet that they manage. |
| Freight Distribution and Logistics Provider | The owner and operator of the Freight Distribution and Logistics Center, ultimately responsible for the functionality that center provides. |
| Freight Equipment Manufacturer | The entity that builds freight equipment. |
| Freight Equipment Monitoring Provider | Application Component Providers are specified more by role than by function. Providers are responsible for the development of the application component, including initial creation, enhancement and bug fixes. Delivery of the application to the end user may require relationships with other entities (installers, maintainers) if the provider chooses not to fulfill those roles. |
| Freight Equipment Owner | The entity that owns freight equipment such as a freight container, intermodal chassis or trailer. |
| Information Service Provider | The "Information Service Provider" represents the owner of the Transportation Information Center. The Information Service Provider is responsible for collecting and disseminating information relevant to the traveling public. |
| Intermodal Customer | The "Intermodal Customer" represents organizations that engage in the shipment of freight, either originator (consigner or shipper) or recipient of the cargo shipment. They enable ITS to move goods on routes that require the use of other modes of transportation such as heavy rail, air, sea, etc. This physical object interfaces with Fleet-Freight Managers to transfer cargo from one mode to another. This definition includes those responsible for the movement of freight across international borders. |
| ITS Certification Entity | The body that determines whether an ITS device or application may be deployed and operated in the transportation environment. This entity's composition, the requirements it applies and the procedures it uses to verify those requirements may vary with device and application type. Typically not a formal body, assigned on a project-by-project basis depending on the type of infrastructure involved. Since ITS projects are locally-focused (typically state or smaller), the entities that are part of this body are typically those with operational jurisdiction where the ITS is installed (e.g., state or local DOTs, state or local maintenance managers etc.) |
| ITS Roadway Equipment Owner | The entity that owns the Roadway ITS equipment. |
| ITS Roadway Operator | The entity that operates the Roadway ITS equipment. |
| Roadway Owner | The owner of the roadway proximate to which roadside equipment will be/is installed. |
| RSE Border Management Installer | Application Component Installers are specified more by role than by function. Installers are responsible for the installation of the application component, which may require a support system, and may entail agreements and relationships between end users and application providers. |
| RSE Border Management Maintainer | Application Component Maintainers are specified more by role than by function. Maintainers are responsible for the maintenance (configuration changes, patches and updates, hardware repairs) of the application component, which may require a support system, and may entail agreements and relationships between end users and application providers. |
| RSE Border Management Provider | Application Component Providers are specified more by role than by function. Providers are responsible for the development of the application component, including initial creation, enhancement and bug fixes. Delivery of the application to the end user may require relationships with other entities (installers, maintainers) if the provider chooses not to fulfill those roles. |
| RSE Deployer | The entity responsible for the deployment, operations and maintenance of roadside equipment. |
| RSE Electronic Screening Installer | Application Component Installers are specified more by role than by function. Installers are responsible for the installation of the application component, which may require a support system, and may entail agreements and relationships between end users and application providers. |
| RSE Electronic Screening Maintainer | Application Component Maintainers are specified more by role than by function. Maintainers are responsible for the maintenance (configuration changes, patches and updates, hardware repairs) of the application component, which may require a support system, and may entail agreements and relationships between end users and application providers. |
| RSE Electronic Screening Provider | Application Component Providers are specified more by role than by function. Providers are responsible for the development of the application component, including initial creation, enhancement and bug fixes. Delivery of the application to the end user may require relationships with other entities (installers, maintainers) if the provider chooses not to fulfill those roles. |
| RSE Operator | The entity that operates roadside equipment in the transportation environment. |
| RSE Owner | The owner of roadside equipment. |
| RSE Provider | The "RSE Provider" is the entity that develops and (presumably) sells roadside equipment to other entities for deployment and research. |
| RSE Traveler Information Communications Installer | Application Component Installers are specified more by role than by function. Installers are responsible for the installation of the application component, which may require a support system, and may entail agreements and relationships between end users and application providers. |
| RSE Traveler Information Communications Maintainer | Application Component Maintainers are specified more by role than by function. Maintainers are responsible for the maintenance (configuration changes, patches and updates, hardware repairs) of the application component, which may require a support system, and may entail agreements and relationships between end users and application providers. |
| RSE Traveler Information Communications Provider | Application Component Providers are specified more by role than by function. Providers are responsible for the development of the application component, including initial creation, enhancement and bug fixes. Delivery of the application to the end user may require relationships with other entities (installers, maintainers) if the provider chooses not to fulfill those roles. |
| State Regulatory | State regulatory bodies that have legal authority to control and/or provide input to policies regulating vehicles, transportation infrastructure and operations. This includes entities like Departments of Motor Vehicles, property tax authorities and tolling agencies. |
| TIC Data Collection Installer | Application Component Installers are specified more by role than by function. Installers are responsible for the installation of the application component, which may require a support system, and may entail agreements and relationships between end users and application providers. |
| TIC Data Collection Maintainer | Application Component Maintainers are specified more by role than by function. Maintainers are responsible for the maintenance (configuration changes, patches and updates, hardware repairs) of the application component, which may require a support system, and may entail agreements and relationships between end users and application providers. |
| TIC Data Collection Provider | Application Component Providers are specified more by role than by function. Providers are responsible for the development of the application component, including initial creation, enhancement and bug fixes. Delivery of the application to the end user may require relationships with other entities (installers, maintainers) if the provider chooses not to fulfill those roles. |
| Traffic Manager | The entity responsible for the management of traffic, both freeway and arterial. |
| Traveler | The 'Traveler' represents any individual who uses transportation services. The interfaces to the traveler provide general pre-trip and en-route information supporting trip planning, personal guidance, and requests for assistance in an emergency that are relevant to all transportation system users. It also represents users of a public transportation system and addresses interfaces these users have within a transit vehicle or at transit facilities such as roadside stops and transit centers. |
| Traveler Card Developer | The entity that develops and manufacturers the traveler card. |
| Vehicle Border Crossing Support Installer | Application Component Installers are specified more by role than by function. Installers are responsible for the installation of the application component, which may require a support system, and may entail agreements and relationships between end users and application providers. |
| Vehicle Border Crossing Support Maintainer | Application Component Maintainers are specified more by role than by function. Maintainers are responsible for the maintenance (configuration changes, patches and updates, hardware repairs) of the application component, which may require a support system, and may entail agreements and relationships between end users and application providers. |
| Vehicle Border Crossing Support Provider | Application Component Providers are specified more by role than by function. Providers are responsible for the development of the application component, including initial creation, enhancement and bug fixes. Delivery of the application to the end user may require relationships with other entities (installers, maintainers) if the provider chooses not to fulfill those roles. |
| Vehicle Manufacturer | The entity that builds, assembles, verifies and validates the Vehicle in which the Vehicle OBE will eventually operate. |
| Vehicle OBE Manufacturer | The entity that builds, assembles, verifies and validates the Vehicle OBE. This can be an OEM-equipped OBE, retrofit or aftermarket equipment. |
| Vehicle OBE Owner | The entity, individual, group or corporation that owns the Vehicle On-Board equipment. This could be the same as the Vehicle Owner, but it could be a third part that licenses the use of the OBE to the Owner. |
| Vehicle Owner | The individual, group of individuals or corporate entity that is identified as the registered owner of the Vehicle under state law. |
Includes Resources:
| Resource | Description |
|---|---|
| Application Component Certification Requirements | The requirements that define the functionality, performance and operational environment of an application component. Certification Requirements must be met in order for an application to be installed in the CVE. |
| Backoffice Service Development System | The systems used to develop backoffice (center) hardware and software components of applications. |
| Backoffice Service Installation System | The systems used to install and configure backoffice (center) hardware and software components. |
| Backoffice Service Maintenance System | The systems used to maintain and upgrade backoffice (center) hardware and software components. |
| Border Inspection | "Border Inspection" manages and supports primary and secondary inspections at the border crossing. |
| Border Inspection Administration | "Border Inspection Administration" performs administrative functions relating to the inspection of goods and vehicles at the border. |
| Border Inspection Administration Center | 'Border Inspection Administration Center' represents back-office systems and databases run by domestic and foreign governmental agencies responsible for the regulation of trade, and the enforcement of customs and immigration laws. These agencies include U.S. Department of Homeland Security (DHS) and its counterparts in Canada and Mexico. DHS includes components like Customs and Border Protection (CBP), Immigration and Customs Enforcement (ICE), and Transportation Security Administration (TSA). Other agencies include secondary trade agencies (e.g., U.S. Food and Drug Administration, U.S. Department of Agriculture, other USDOT departments, etc.), and agencies from other trading nations. The systems they manage coordinate activities related to the border crossings. These systems support import/export cargo processing and enforcement operations at the border, including programs such as FAST, Automated Commercial Environment (ACE), Nexus (Canada), SENTRI (Mexico), and US-VISIT. |
| Border Inspection System | 'Border Inspection System' represents data systems used at the border for the inspection of people or goods. It supports immigration, customs (trade), agricultural, and FDA inspections as applicable. It includes sensors and surveillance systems to identify and classify drivers and their cargo as they approach a border crossing, the systems used to interface with the back-office administration systems and provide information on status of the crossing or events. |
| Commercial Vehicle | The commercial vehicle includes the sensory, processing, storage, and communications functions necessary to support safe and efficient commercial vehicle operations. It includes two-way communications between the commercial vehicle drivers, their fleet managers, attached freight equipment, and roadside officials, and provides HAZMAT response teams with timely and accurate cargo contents information after a vehicle incident. It can collect and process vehicle, cargo information from the attached freight equipment, and driver safety data and status and alert the driver whenever there is a potential safety or security problem. Basic identification, security and safety status data are supplied to inspection facilities at mainline speeds. In addition, it can automatically collect and record mileage, fuel usage, and border crossings. |
| Commercial Vehicle Administration Center | The 'Commercial Vehicle Administration Center' performs administrative functions supporting credentials, tax, and safety regulations associated with commercial vehicles. It issues credentials, collects fees and taxes, and supports enforcement of credential requirements. It communicates with motor carriers to process credentials applications and collect fuel taxes, weight/distance taxes, and other taxes and fees associated with commercial vehicle operations. It also receives applications for, and issues special Oversize/Overweight and HAZMAT permits in coordination with cognizant authorities. It coordinates with other Commercial Vehicle Administration Centers (in other states/regions) to support nationwide access to credentials and safety information for administration and enforcement functions. It communicates with field equipment to enable credential checking and safety information collection at the roadside. It makes safety information available to qualified stakeholders to identify carriers and drivers that operate unsafely. |
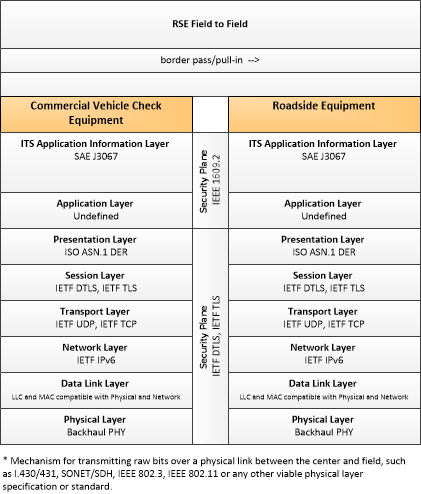
| Commercial Vehicle Check Equipment | 'Commercial Vehicle Check Equipment' supports automated vehicle identification at mainline speeds for credential checking, roadside safety inspections, and weigh-in-motion using two-way data exchange. These capabilities include providing warnings to the commercial vehicle drivers, their fleet managers, and proper authorities of any safety problems that have been identified, accessing and examining historical safety data, and automatically deciding whether to allow the vehicle to pass or require it to stop with operator manual override. Commercial Vehicle Check Equipment also provides supplemental inspection services such as expedited brake inspections, the use of operator hand-held devices, mobile screening sites, on-board safety database access, and the enrollment of vehicles and carriers in the electronic clearance program. |
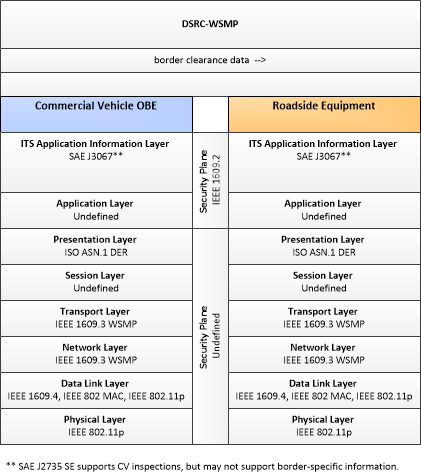
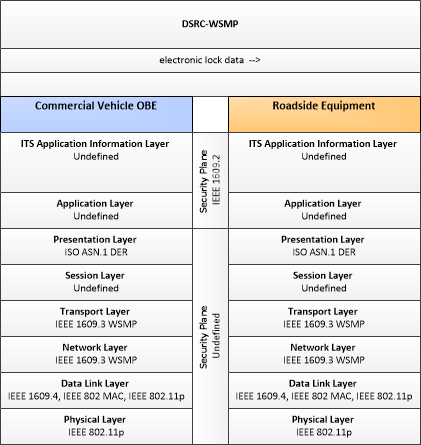
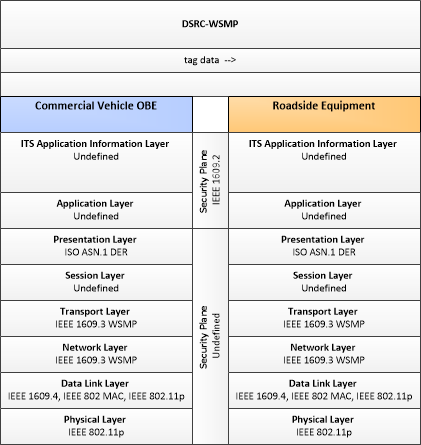
| Commercial Vehicle OBE | The Commercial Vehicle On-Board Equipment (OBE) resides in a commercial vehicle and provides the sensory, processing, storage, and communications functions necessary to support safe and efficient commercial vehicle operations. It provides two-way communications between the commercial vehicle drivers, their fleet managers, attached freight equipment, and roadside officials. In CVRIA, a separate 'Vehicle OBE' physical object supports the general V2V and V2I safety applications and other applications that apply to all vehicles, including commercial vehicles. The Commercial Vehicle OBE supplements these general capabilities with capabilities that are specific to commercial vehicles. |
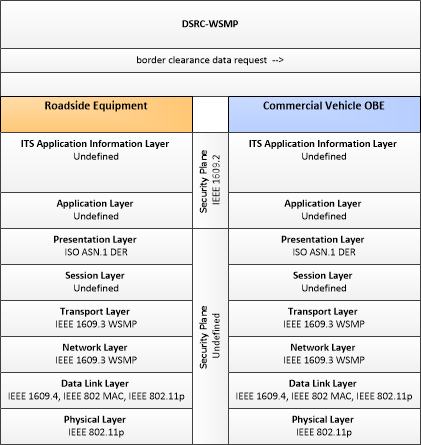
| CV On-Board Electronic Screening Support | "CV On-Board Electronic Screening Support" exchanges information with roadside facilities, providing information such as driver, vehicle, and carrier identification to roadside facilities that can be used to support electronic screening. Pass/pull-in messages are received and presented to the commercial vehicle driver and screening events are recorded. Additional information, including trip records (e.g., border clearance information), safety inspection records, cargo information, and driver status information may also be collected, stored, and made available to the roadside facility. |
| CVAC Information Exchange | "CVAC Information Exchange" supports the exchange of safety, credentials, permit data, and other data concerning the operation of commercial vehicles among jurisdictions. The package also supports the exchange of safety, credentials, permit, and operations data between systems (for example, an administrative center and the roadside check facilities) within a single jurisdiction. Data are collected from multiple authoritative sources and packaged into snapshots (top-level summary and critical status information) and profiles (detailed and historical data). Data is made available to fleet operators and other information requestors on request or based on subscriptions established by the requestor. |
| CVAC International Administration | "CVAC International Administration" generates and processes the entry documentation necessary to obtain release of vehicle, cargo, and driver across an international border, report the results of the crossing event, and handle duty fee processing. It interfaces with the systems used by customs and border protection, immigration, carriers, and service providers (e.g., brokers) to generate, process, and store entry documentation. |
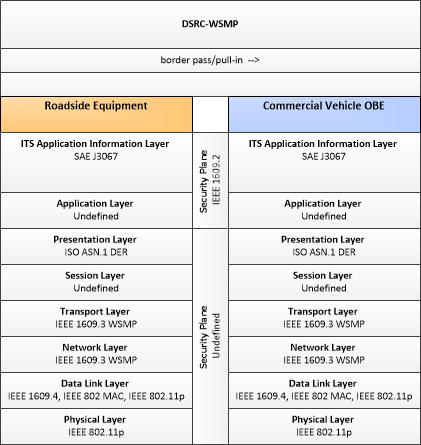
| CVCE Electronic Screening | "CVCE Electronic Screening" supports electronic credentials and safety screening of commercial vehicles at mainline speeds. It processes the data from the commercial vehicles along with accessed database information to determine whether a pull-in message is needed. It may also generate random pull-in messages with provisions for facility operators and enforcement officials to have manual override capabilities. |
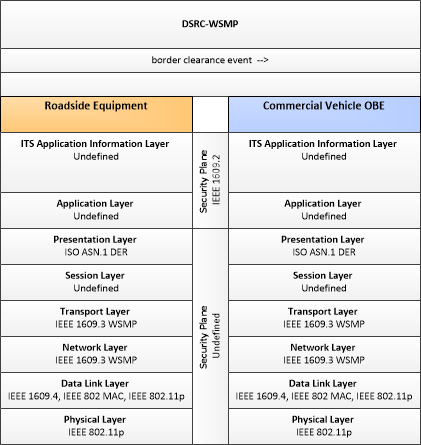
| CVCE International Border Crossing | "CVCE International Border Crossing" checks compliance with import/export and immigration regulations to manage release of commercial vehicle, cargo, and driver across an international border. It includes interfaces to the equipment at international border crossings operated by government agencies such as Customs and Border Protection. |
| Device Certification Requirements | The requirements that define the functionality, performance and operational environment of a connected vehicle device. Certification Requirements must be met in order for the device to be granted the credentials necessary to operate in the Connected Vehicle Environment. |
| Drayage Operations Optimization Service | The "Drayage Operations Optimization Service" provides a portal for shippers and receivers to post their loads in need of transport and provide an opportunity for commercial vehicles to find a load to haul on their trip back to/from an intermodal facility. It connects load matching services with container and chassis/equipment availability information and appointment/reservations services from the intermodal terminals to provide an optimized, regionally integrated view of intermodal container transport for drayage operators. |
| Field Component Development System | The system used in a backoffice environment to develop and test the field component of the application. |
| Field Component Installation System | The system used to install a field component of a connected vehicle application. |
| Field Component Maintenance System | The system used to install and configure changes and updates to the field component of the application. This system is capable of acquiring and reporting diagnostic information about the application's configuration and performance. |
| Fleet and Freight Management Center | The 'Fleet and Freight Management Center' provides the capability for commercial drivers and fleet-freight managers to receive real-time routing information and access databases containing vehicle and/or freight equipment locations as well as carrier, vehicle, freight equipment and driver information. The 'Fleet and Freight Management Center' also provides the capability for fleet managers to monitor the safety and security of their commercial vehicle drivers and fleet. |
| Freight Distribution and Logistics Center | The 'Freight Distribution and Logistics Center' provides intermodal logistics support and support for the efficient distribution of freight across transport systems and modes. This can include consolidation arrangements, warehousing, and consignor-to-consignee intermodal shipping arrangements. These capabilities may be provided as part of intermodal fleet management activities or can be provided by an independent logistics specialist. |
| Freight Equipment | 'Freight Equipment' represents a freight container, intermodal chassis, or trailer and provides sensory, processing, storage, and communications functions necessary to support safe, secure and efficient freight operations. It provides equipment safety data and status and can alert the appropriate systems of an incident, breach, or tamper event. It also provides accurate position information to support in-transit visibility of freight equipment. |
| Intermodal Customer System | The 'Intermodal Customer System' represents organizations that engage in the shipment of freight, either originator (consigner or shipper) or recipient of the cargo shipment. They enable the movement of goods on routes that require the use of other modes of transportation such as heavy rail, air, sea, etc. The Intermodal Customer System includes those personnel responsible for the movement of freight across international borders. |
| ITS Certification Requirements | The requirements that define the functionality, performance and operational environment of an ITS device or ITS application. Applicability varies with jurisdictions, but typically devices and applications must meet pre-defined acceptance criteria prior to usage in the transportation environment. |
| ITS Field Component Development System | The system used in a backoffice environment to develop and test the ITS field component of the application. |
| ITS Field Component Installation System | The system used to install a field component of a connected vehicle application. |
| ITS Field Component Maintenance System | The system used to install and configure changes and updates to the ITS field component of the application. This system is capable of acquiring and reporting diagnostic information about the application's configuration and performance. |
| Mobile Component Development System | The system used in a backoffice environment to develop and test the mobile component of the application. |
| Mobile Component Installation System | The system that interacts with the Vehicle OBE other mobile device and installs the mobile component of the application. |
| Mobile Component Maintenance System | The system used to configure changes and updates to the mobile component of the application. This system is capable of acquiring and reporting diagnostic information about the application's configuration and performance. |
| Roadside Equipment | 'Roadside Equipment' (RSE) represents the Connected Vehicle roadside devices that are used to send messages to, and receive messages from, nearby vehicles using Dedicated Short Range Communications (DSRC) or other alternative wireless communications technologies. Communications with adjacent field equipment and back office centers that monitor and control the RSE are also supported. This device operates from a fixed position and may be permanently deployed or a portable device that is located temporarily in the vicinity of a traffic incident, road construction, or a special event. It includes a processor, data storage, and communications capabilities that support secure communications with passing vehicles, other field equipment, and centers. |
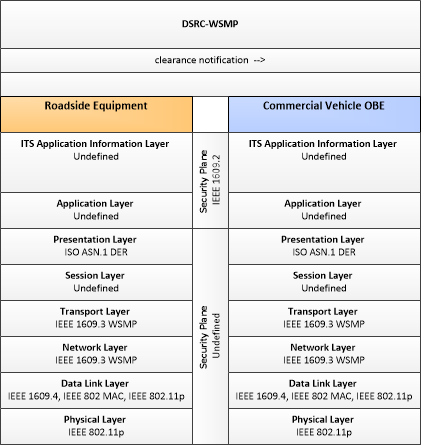
| RSE Border Management | "RSE Border Management" supports border operations, providing functions that measure border wait times and provide wait times and other traveler information to approaching vehicles. Short range communications with vehicles and associated equipment supports collection of traveler, vehicle, and cargo information and credentials. |
| RSE Development System | The system used in a backoffice environment to develop and test the roadside equipment. |
| RSE Electronic Screening | "RSE Electronic Screening" provides two-way communication with approaching properly equipped commercial vehicles at mainline speeds for automated vehicle identification and credential checking. |
| RSE Installation System | The system used to install and configure the roadside equipment. |
| RSE Maintenance System | The system used to configure changes and updates to the roadside equipment. This system is capable of acquiring and reporting diagnostic information about the RSE's configuration and performance. |
| RSE Traveler Information Communications | "RSE Traveler Information Communications" includes field elements that distribute information to vehicles for in-vehicle display. The information may be provided by a center (e.g., variable information on traffic and road conditions in the vicinity of the field equipment) or it may be determined and output locally (e.g., static sign information and signal phase and timing information). This includes the interface to the center or field equipment that controls the information distribution and the short range communications equipment that provides information to passing vehicles. |
| TIC Data Collection | "TIC Data Collection" collects transportation-related data from other centers, performs data quality checks on the collected data and then consolidates, verifies, and refines the data and makes it available in a consistent format to applications that support operational data sharing between centers and deliver traveler information to end-users. A broad range of data is collected including traffic and road conditions, transit data, emergency information and advisories, weather data, special event information, traveler services, parking, multimodal data, and toll/pricing data. It also shares data with other transportation information centers. |
| Traffic Management Center | The 'Traffic Management Center' monitors and controls traffic and the road network. It represents centers that manage a broad range of transportation facilities including freeway systems, rural and suburban highway systems, and urban and suburban traffic control systems. It communicates with ITS Roadway Equipment and Connected Vehicle Roadside Equipment (RSE) to monitor and manage traffic flow and monitor the condition of the roadway, surrounding environmental conditions, and field equipment status. It manages traffic and transportation resources to support allied agencies in responding to, and recovering from, incidents ranging from minor traffic incidents through major disasters. |
| Transportation Information Center | The 'Transportation Information Center' collects, processes, stores, and disseminates transportation information to system operators and the traveling public. The physical object can play several different roles in an integrated ITS. In one role, the TIC provides a data collection, fusing, and repackaging function, collecting information from transportation system operators and redistributing this information to other system operators in the region and other TICs. In this information redistribution role, the TIC provides a bridge between the various transportation systems that produce the information and the other TICs and their subscribers that use the information. The second role of a TIC is focused on delivery of traveler information to subscribers and the public at large. Information provided includes basic advisories, traffic and road conditions, transit schedule information, yellow pages information, ride matching information, and parking information. The TIC is commonly implemented as a website or a web-based application service, but it represents any traveler information distribution service. |
| Traveler Card | The 'Traveler Card' stores traveler identification information, including biometric information, that can be used in trusted traveler programs to expedite clearance through security checkpoints at borders or security-critical areas. |
| Vehicle | The conveyance that provides the sensory, processing, storage, and communications functions necessary to support efficient, safe, and convenient travel. These functions reside in general vehicles including personal automobiles, commercial vehicles, emergency vehicles, transit vehicles, or other vehicle types. |
| Vehicle Border Crossing Support | "Vehicle Border Crossing Support" uses connected vehicle technology to exchange traveler credentials with border systems to support expedited clearance through international borders. |
| Vehicle OBE | The Vehicle On-Board Equipment (OBE) provides the vehicle-based processing, storage, and communications functions necessary to support connected vehicle operations. The radio(s) supporting V2V and V2I communications are a key component of the Vehicle OBE. This communication platform is augmented with processing and data storage capability that supports the connected vehicle applications. In CVRIA, the Vehicle OBE includes the functions and interfaces that support connected vehicle applications for passenger cars, trucks, and motorcycles. Many of these applications (e.g., V2V Safety applications) apply to all vehicle types including personal vehicles, commercial vehicles, emergency vehicles, transit vehicles, and maintenance vehicles. From this perspective, the Vehicle OBE includes the common interfaces and functions that apply to all motorized vehicles. |
Includes Roles:
| Role | Description |
|---|---|
| Certifies | An Enterprise verifies that a target Resource meets relevant performance, functional, environmental and quality requirements. |
| Constrains | A Resource or Enterprise applies requirements, constraints and associated tests to another Resource. |
| Develops | An Enterprise creates the target Resource or Document. |
| Installs | An Enterprise performs the initial delivery, integration and configuration of the target Resource. |
| Maintains | An Enterprise administers the hardware and software that comprise the target Resource. |
| Member | An Enterprise is part of another larger, target Enterprise. |
| Operates | An Enterprise controls the functionality and state of the target Resource. An Enterprise that Operates a resource is considered Responsible. |
| Owns | An Enterprise has financial ownership and control over the Resource. An Enterprise that Owns a resource is considered Accountable. |
Includes Coordination:
| Coordination | Type | Description |
|---|---|---|
| Application Installation Data | Information Sharing | Data needed to install the application, including the application executable code and any configuration data. Unidirectional flow. |
| Application Interface Specification | Agreement | The definition of an interface between two application components that operate on two distinct pieces of hardware. The Application Interface Specification is specific to the application in question. |
| Application Maintenance Data | Information Sharing | Data used to facilitate the upgrade, patching and general health maintenance of an application component. |
| Application Performance Data | Information Sharing | Data used to characterize application performance, including such measures as availability, known errors and known uses. |
| Application Procurement Agreement | Agreement | An agreement whereupon one entity provides a copy of an application component to another entity. This component is capable of being installed and functioning, according to its requirements that passed through the application's certification process. |
| Application Usage Agreement | Agreement | An agreement in which one entity that controls an application component's use gives the other entity the necessary tools and permission to operate that application or application component. |
| Backoffice Component Installation Agreement | Agreement | An agreement that grants one party permission to install a backoffice application component on a center-based device controlled by the other party. |
| Backoffice Component Maintenance Agreement | Agreement | An agreement in which one entity maintains the operational status of the backoffice component of an application under the control of another entity. This maintenance may include routine and as-needed maintenance, such as software update and configuration, hardware replacement and related system administration activities. |
| Device Placement and Operations Agreement | Agreement | An agreement that enables the controller of a physical device to install it (so as to make it operational) at a fixed location controlled by another entity. |
| Expectation of Data Provision | Expectation | An expectation where one party believes another party will provide data on a regular and recurring basis, and that that data will be useful to the receiver in the context of the receiver's application. This thus includes some expectation of data fields, timeliness, quality, precision and similar qualities of data. |
| Expectation of Information Provision | Expectation | An expectation where one party believes another party will provide it information whenever such information is likely relevant to the recipient. |
| Field Component Installation Agreement | Agreement | An agreement that grants one party permission to install a field application component on a roadside device controlled by the other party. |
| Field Component Maintenance Agreement | Agreement | An agreement in which one entity maintains the operational status of the field component of an application under the control of another entity. This maintenance may include routine and as-needed maintenance, such as software update and configuration, hardware replacement and related system administration activities. |
| Includes | Includes | Indicates that one component is entirely contained within another component. |
| Information Exchange Agreement | Agreement | An agreement to exchange information, which may include data or control information; the exact information to be exchanged may vary from agreement to agreement. |
| Information Exchange and Action Agreement | Agreement | An agreement to exchange information, which may include data or control information; the exact information to be exchanged may vary from agreement to agreement. This also includes a specification for action that shall, should or may be taken by one party in response to this information. |
| Information Provision Agreement | Agreement | An agreement where one party agrees to provide information to another party. This is a unidirectional agreement. |
| Installation Agreement | Agreement | An agreement whereupon one entity installs an application component on a device controlled by another entity. |
| Interface Description | Agreement | Documentation of the interface between two systems, where one system does not have an application component that is part of the application, but does provide and/or receive data and/or information that is used by or sourced from the application. In many cases this is an existing interface used by the application, so the description of the interface already exists and is imposed by the terminator. |
| Maintenance Agreement | Agreement | An agreement in which one entity maintains the operational status of a system under the control of another entity. This maintenance may include routine and as-needed maintenance, such as software update and configuration, hardware replacement and related system administration activities. |
| Maintenance Data Exchange Agreement | Agreement | An agreement that states one entity will provide data related to maintenance of an application component to the other entity. |
| Mobile Component Installation Agreement | Agreement | An agreement whereupon the controller of OBE gives another party permission to install, configure and make operational a component that enables the mobile portion of an application. |
| Mobile Component License Agreement | Agreement | An end-user license agreement allowing the operator of the mobile device to use the mobile application component that is part of the application in question. |
| Mobile Component Maintenance Agreement | Agreement | An agreement in which one entity maintains the operational status of the mobile component of an application under the control of another entity. This maintenance may include routine and as-needed maintenance, such as software update and configuration, hardware replacement and related system administration activities. |
| Operations Agreement | Agreement | An agreement where one entity agrees to operate a device or application on behalf of another, device/application controlling entity. |
| RSE Deployment Agreement | Agreement | Agreement to install, configure and make operational roadside equipment, between the provider of that equipment and the entity that controls access to the roadside. May define locations, expectation of power provision, backhaul responsibility and installation restrictions. |
| RSE Installation Data | Information Sharing | Data necessary to configure and make RSE operational. Uni-directional. |
| RSE Maintenance Data | Information Sharing | Data necessary to modify the operational configuration of RSE; assumes RSE is already configured. Uni-directional. |
| RSE Performance Data | Information Sharing | Data that includes metrics of RSE performance. Could include fields such as uptime, packets received/transmitted, distance vector from which packets received, as well as application-specific performance measures. |
| RSE Procurement Agreement | Agreement | An agreement whereupon one entity provides roadside equipment to another entity. The RSE is capable of being installed and functioning, according to its requirements that passed through the device's certification process. |
| Service Delivery Agreement | Agreement | A relationship where one party agrees to provide a service to the other party. This agreement may specify the expected performance of this service in terms of availability and/or actions/time-type performance specifications. |
| Vehicle Data Access Agreement | Agreement | An agreement whereby the party that controls access to on-board vehicle data grants another party the right and ability to access that data. Includes the conditions under which data may be accessed, and specifies the mechanisms, including physical and functional access methods, data formats and any other considerations necessary for the accessing party to acquire data. May also include caveats regarding responsibility for data quality and responsibility for use of the data. |
| Vehicle OBE Usage Agreement | Agreement | An agreement that grants one entity permission to use a Vehicle OBE that the other party controls. |
| Vehicle Operating Agreement | Agreement | An agreement whereupon the controller of a vehicle grants another entity permission and rights to operate the vehicle. |
| Vehicle Procurement Agreement | Agreement | The exchange of a vehicle for compensation. One entity purchases the vehicle from the other. |
| Vehicle Usage Agreement | Agreement | An agreement between the owner of a vehicle and a prospective operator, whereupon the owner allows the operator to use the vehicle. |
| Warranty | Agreement | A guarantee or promise made by one entity to another, that provides assurance of the functionality and performance over time of an application component. |
Functional
Includes Processes:
Includes Data Flows:
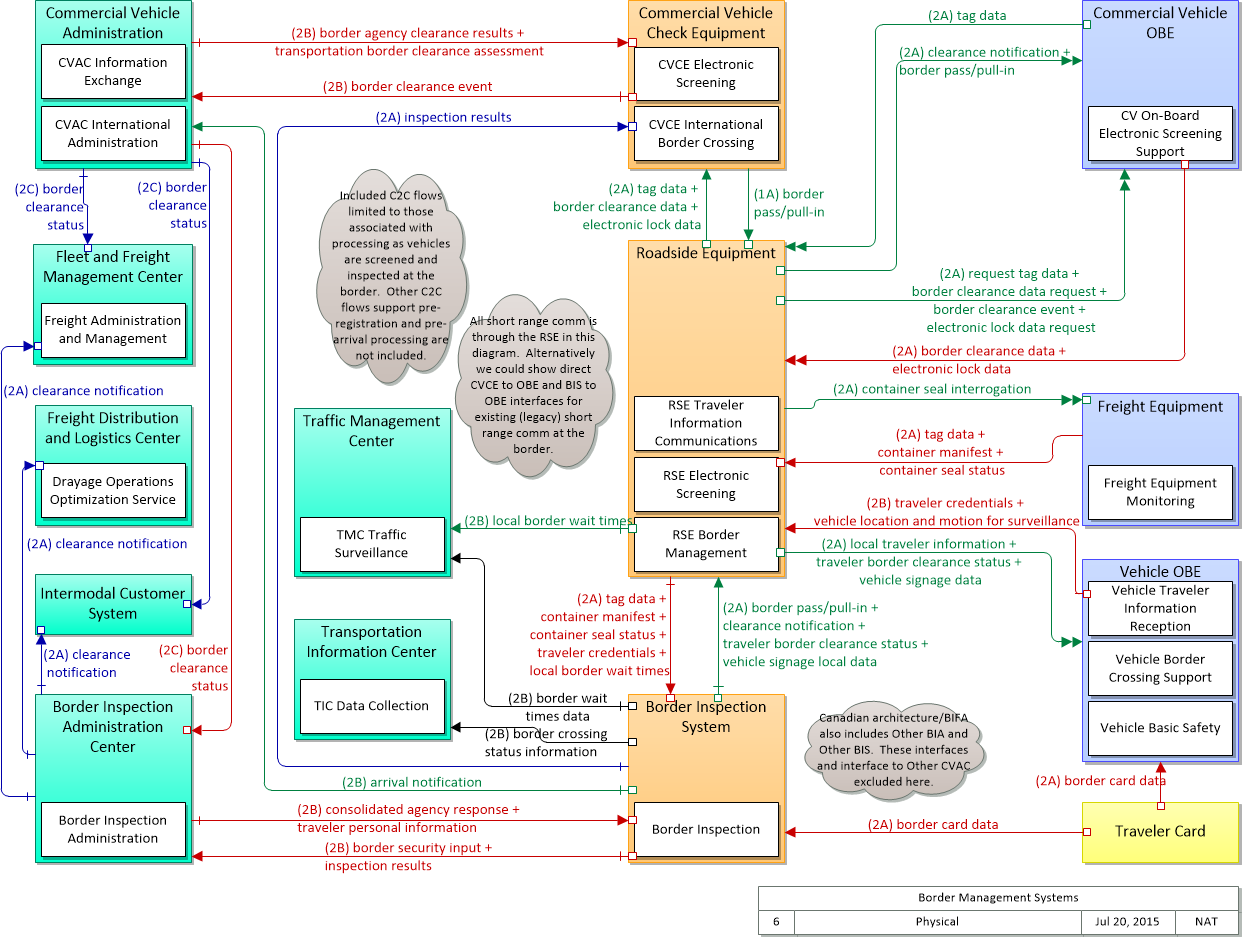
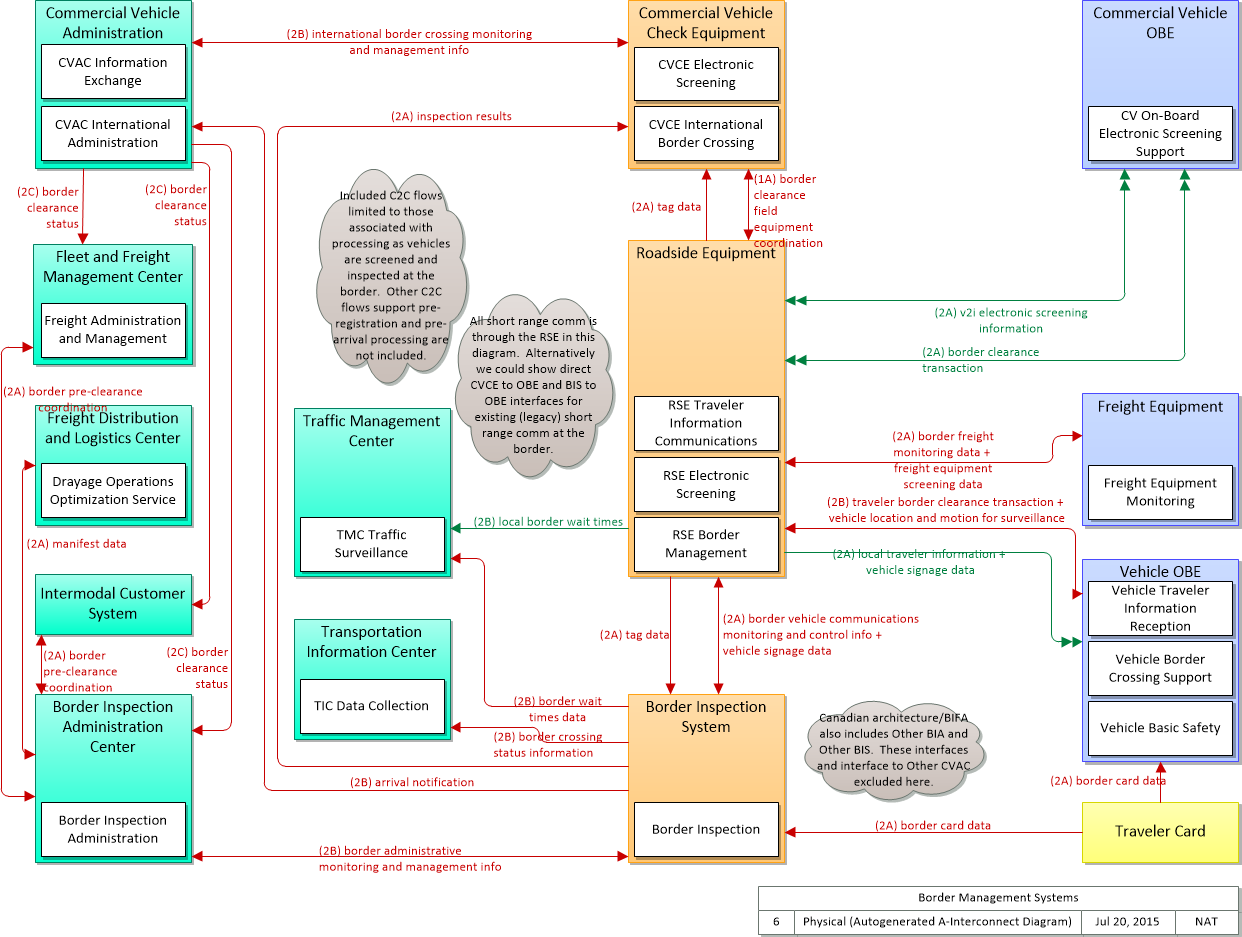
Physical
This is one way this application may be realized, but not the only way. There are other ways to build a given application and accomplish a stated objective.
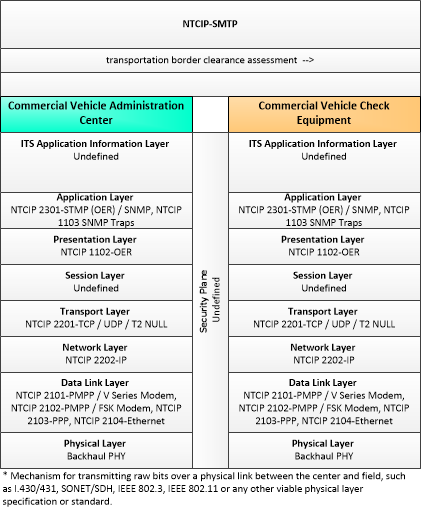
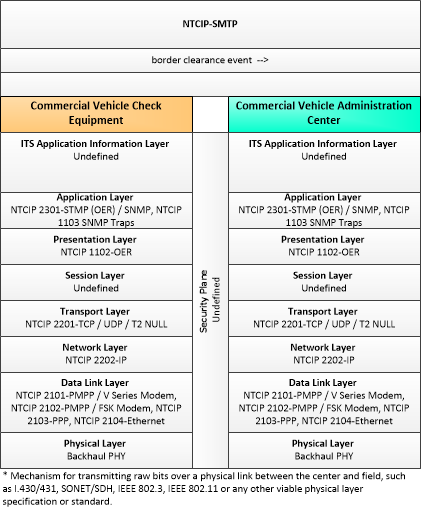
The physical diagram can be viewed in SVG or PNG format and the current format is SVG. SVG Diagram
PNG Diagram
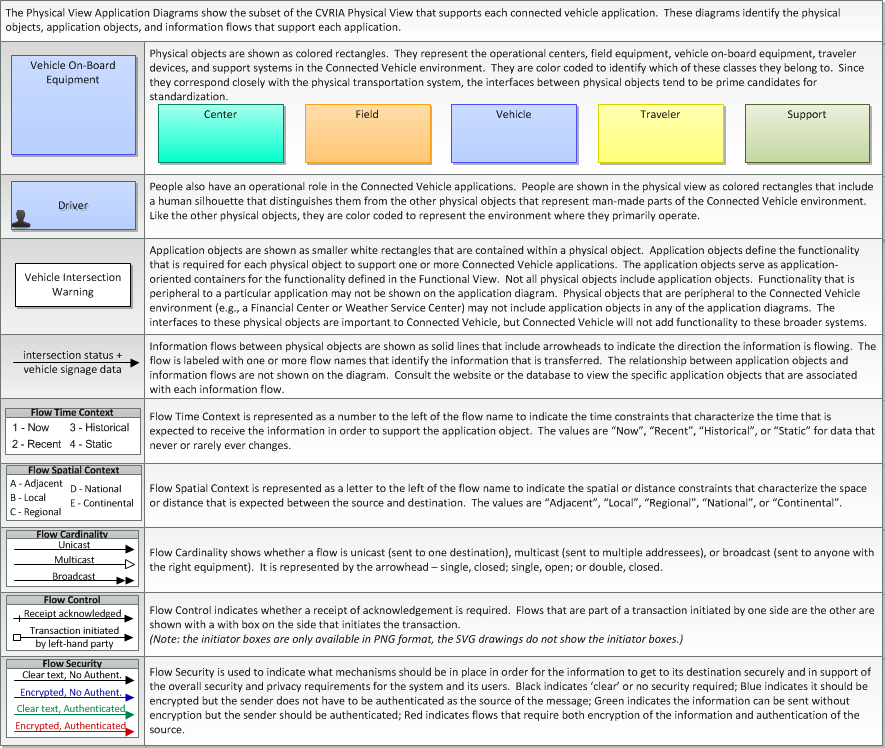
Includes Physical Objects:
| Physical Object | Class | Description |
|---|---|---|
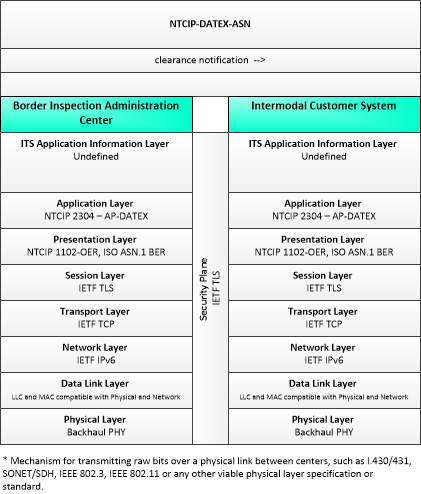
| Border Inspection Administration Center | Center | 'Border Inspection Administration Center' represents back-office systems and databases run by domestic and foreign governmental agencies responsible for the regulation of trade, and the enforcement of customs and immigration laws. These agencies include U.S. Department of Homeland Security (DHS) and its counterparts in Canada and Mexico. DHS includes components like Customs and Border Protection (CBP), Immigration and Customs Enforcement (ICE), and Transportation Security Administration (TSA). Other agencies include secondary trade agencies (e.g., U.S. Food and Drug Administration, U.S. Department of Agriculture, other USDOT departments, etc.), and agencies from other trading nations. The systems they manage coordinate activities related to the border crossings. These systems support import/export cargo processing and enforcement operations at the border, including programs such as FAST, Automated Commercial Environment (ACE), Nexus (Canada), SENTRI (Mexico), and US-VISIT. |
| Border Inspection System | Field | 'Border Inspection System' represents data systems used at the border for the inspection of people or goods. It supports immigration, customs (trade), agricultural, and FDA inspections as applicable. It includes sensors and surveillance systems to identify and classify drivers and their cargo as they approach a border crossing, the systems used to interface with the back-office administration systems and provide information on status of the crossing or events. |
| Commercial Vehicle Administration Center | Center | The 'Commercial Vehicle Administration Center' performs administrative functions supporting credentials, tax, and safety regulations associated with commercial vehicles. It issues credentials, collects fees and taxes, and supports enforcement of credential requirements. It communicates with motor carriers to process credentials applications and collect fuel taxes, weight/distance taxes, and other taxes and fees associated with commercial vehicle operations. It also receives applications for, and issues special Oversize/Overweight and HAZMAT permits in coordination with cognizant authorities. It coordinates with other Commercial Vehicle Administration Centers (in other states/regions) to support nationwide access to credentials and safety information for administration and enforcement functions. It communicates with field equipment to enable credential checking and safety information collection at the roadside. It makes safety information available to qualified stakeholders to identify carriers and drivers that operate unsafely. |
| Commercial Vehicle Check Equipment | Field | 'Commercial Vehicle Check Equipment' supports automated vehicle identification at mainline speeds for credential checking, roadside safety inspections, and weigh-in-motion using two-way data exchange. These capabilities include providing warnings to the commercial vehicle drivers, their fleet managers, and proper authorities of any safety problems that have been identified, accessing and examining historical safety data, and automatically deciding whether to allow the vehicle to pass or require it to stop with operator manual override. Commercial Vehicle Check Equipment also provides supplemental inspection services such as expedited brake inspections, the use of operator hand-held devices, mobile screening sites, on-board safety database access, and the enrollment of vehicles and carriers in the electronic clearance program. |
| Commercial Vehicle OBE | Vehicle | The Commercial Vehicle On-Board Equipment (OBE) resides in a commercial vehicle and provides the sensory, processing, storage, and communications functions necessary to support safe and efficient commercial vehicle operations. It provides two-way communications between the commercial vehicle drivers, their fleet managers, attached freight equipment, and roadside officials. In CVRIA, a separate 'Vehicle OBE' physical object supports the general V2V and V2I safety applications and other applications that apply to all vehicles, including commercial vehicles. The Commercial Vehicle OBE supplements these general capabilities with capabilities that are specific to commercial vehicles. |
| Fleet and Freight Management Center | Center | The 'Fleet and Freight Management Center' provides the capability for commercial drivers and fleet-freight managers to receive real-time routing information and access databases containing vehicle and/or freight equipment locations as well as carrier, vehicle, freight equipment and driver information. The 'Fleet and Freight Management Center' also provides the capability for fleet managers to monitor the safety and security of their commercial vehicle drivers and fleet. |
| Freight Distribution and Logistics Center | Center | The 'Freight Distribution and Logistics Center' provides intermodal logistics support and support for the efficient distribution of freight across transport systems and modes. This can include consolidation arrangements, warehousing, and consignor-to-consignee intermodal shipping arrangements. These capabilities may be provided as part of intermodal fleet management activities or can be provided by an independent logistics specialist. |
| Freight Equipment | Vehicle | 'Freight Equipment' represents a freight container, intermodal chassis, or trailer and provides sensory, processing, storage, and communications functions necessary to support safe, secure and efficient freight operations. It provides equipment safety data and status and can alert the appropriate systems of an incident, breach, or tamper event. It also provides accurate position information to support in-transit visibility of freight equipment. |
| Intermodal Customer System | Center | The 'Intermodal Customer System' represents organizations that engage in the shipment of freight, either originator (consigner or shipper) or recipient of the cargo shipment. They enable the movement of goods on routes that require the use of other modes of transportation such as heavy rail, air, sea, etc. The Intermodal Customer System includes those personnel responsible for the movement of freight across international borders. |
| Roadside Equipment | Field | 'Roadside Equipment' (RSE) represents the Connected Vehicle roadside devices that are used to send messages to, and receive messages from, nearby vehicles using Dedicated Short Range Communications (DSRC) or other alternative wireless communications technologies. Communications with adjacent field equipment and back office centers that monitor and control the RSE are also supported. This device operates from a fixed position and may be permanently deployed or a portable device that is located temporarily in the vicinity of a traffic incident, road construction, or a special event. It includes a processor, data storage, and communications capabilities that support secure communications with passing vehicles, other field equipment, and centers. |
| Traffic Management Center | Center | The 'Traffic Management Center' monitors and controls traffic and the road network. It represents centers that manage a broad range of transportation facilities including freeway systems, rural and suburban highway systems, and urban and suburban traffic control systems. It communicates with ITS Roadway Equipment and Connected Vehicle Roadside Equipment (RSE) to monitor and manage traffic flow and monitor the condition of the roadway, surrounding environmental conditions, and field equipment status. It manages traffic and transportation resources to support allied agencies in responding to, and recovering from, incidents ranging from minor traffic incidents through major disasters. |
| Transportation Information Center | Center | The 'Transportation Information Center' collects, processes, stores, and disseminates transportation information to system operators and the traveling public. The physical object can play several different roles in an integrated ITS. In one role, the TIC provides a data collection, fusing, and repackaging function, collecting information from transportation system operators and redistributing this information to other system operators in the region and other TICs. In this information redistribution role, the TIC provides a bridge between the various transportation systems that produce the information and the other TICs and their subscribers that use the information. The second role of a TIC is focused on delivery of traveler information to subscribers and the public at large. Information provided includes basic advisories, traffic and road conditions, transit schedule information, yellow pages information, ride matching information, and parking information. The TIC is commonly implemented as a website or a web-based application service, but it represents any traveler information distribution service. |
| Traveler Card | Traveler | The 'Traveler Card' stores traveler identification information, including biometric information, that can be used in trusted traveler programs to expedite clearance through security checkpoints at borders or security-critical areas. |
| Vehicle OBE | Vehicle | The Vehicle On-Board Equipment (OBE) provides the vehicle-based processing, storage, and communications functions necessary to support connected vehicle operations. The radio(s) supporting V2V and V2I communications are a key component of the Vehicle OBE. This communication platform is augmented with processing and data storage capability that supports the connected vehicle applications. In CVRIA, the Vehicle OBE includes the functions and interfaces that support connected vehicle applications for passenger cars, trucks, and motorcycles. Many of these applications (e.g., V2V Safety applications) apply to all vehicle types including personal vehicles, commercial vehicles, emergency vehicles, transit vehicles, and maintenance vehicles. From this perspective, the Vehicle OBE includes the common interfaces and functions that apply to all motorized vehicles. |
Includes Application Objects:
| Application Object | Description | Physical Object |
|---|---|---|
| Border Inspection | "Border Inspection" manages and supports primary and secondary inspections at the border crossing. | Border Inspection System |
| Border Inspection Administration | "Border Inspection Administration" performs administrative functions relating to the inspection of goods and vehicles at the border. | Border Inspection Administration Center |
| CV On-Board Electronic Screening Support | "CV On-Board Electronic Screening Support" exchanges information with roadside facilities, providing information such as driver, vehicle, and carrier identification to roadside facilities that can be used to support electronic screening. Pass/pull-in messages are received and presented to the commercial vehicle driver and screening events are recorded. Additional information, including trip records (e.g., border clearance information), safety inspection records, cargo information, and driver status information may also be collected, stored, and made available to the roadside facility. | Commercial Vehicle OBE |
| CVAC Information Exchange | "CVAC Information Exchange" supports the exchange of safety, credentials, permit data, and other data concerning the operation of commercial vehicles among jurisdictions. The package also supports the exchange of safety, credentials, permit, and operations data between systems (for example, an administrative center and the roadside check facilities) within a single jurisdiction. Data are collected from multiple authoritative sources and packaged into snapshots (top-level summary and critical status information) and profiles (detailed and historical data). Data is made available to fleet operators and other information requestors on request or based on subscriptions established by the requestor. | Commercial Vehicle Administration Center |
| CVAC International Administration | "CVAC International Administration" generates and processes the entry documentation necessary to obtain release of vehicle, cargo, and driver across an international border, report the results of the crossing event, and handle duty fee processing. It interfaces with the systems used by customs and border protection, immigration, carriers, and service providers (e.g., brokers) to generate, process, and store entry documentation. | Commercial Vehicle Administration Center |
| CVCE Electronic Screening | "CVCE Electronic Screening" supports electronic credentials and safety screening of commercial vehicles at mainline speeds. It processes the data from the commercial vehicles along with accessed database information to determine whether a pull-in message is needed. It may also generate random pull-in messages with provisions for facility operators and enforcement officials to have manual override capabilities. | Commercial Vehicle Check Equipment |
| CVCE International Border Crossing | "CVCE International Border Crossing" checks compliance with import/export and immigration regulations to manage release of commercial vehicle, cargo, and driver across an international border. It includes interfaces to the equipment at international border crossings operated by government agencies such as Customs and Border Protection. | Commercial Vehicle Check Equipment |
| Drayage Operations Optimization Service | The "Drayage Operations Optimization Service" provides a portal for shippers and receivers to post their loads in need of transport and provide an opportunity for commercial vehicles to find a load to haul on their trip back to/from an intermodal facility. It connects load matching services with container and chassis/equipment availability information and appointment/reservations services from the intermodal terminals to provide an optimized, regionally integrated view of intermodal container transport for drayage operators. | Freight Distribution and Logistics Center |
| Freight Administration and Management | "Freight Administration and Management" manages the movement of freight from source to destination. It interfaces to intermodal customers to setup and schedule transportation and coordinates with intermodal terminals and freight consolidation stations to coordinate the shipment. It coordinates with the appropriate government agencies to expedite the movement of trucks, their drivers, and their cargo across international borders. The application monitors the status of the freight and freight equipment (container, trailer, or chassis) and monitors freight location and compares it against the planned route. | Fleet and Freight Management Center |
| Freight Equipment Monitoring | "Freight Equipment Monitoring" includes the on-board devices used to monitor intermodal freight equipment. These devices provide freight equipment location and status of the freight, container, or chassis equipment. | Freight Equipment |
| RSE Border Management | "RSE Border Management" supports border operations, providing functions that measure border wait times and provide wait times and other traveler information to approaching vehicles. Short range communications with vehicles and associated equipment supports collection of traveler, vehicle, and cargo information and credentials. | Roadside Equipment |
| RSE Electronic Screening | "RSE Electronic Screening" provides two-way communication with approaching properly equipped commercial vehicles at mainline speeds for automated vehicle identification and credential checking. | Roadside Equipment |
| RSE Traveler Information Communications | "RSE Traveler Information Communications" includes field elements that distribute information to vehicles for in-vehicle display. The information may be provided by a center (e.g., variable information on traffic and road conditions in the vicinity of the field equipment) or it may be determined and output locally (e.g., static sign information and signal phase and timing information). This includes the interface to the center or field equipment that controls the information distribution and the short range communications equipment that provides information to passing vehicles. | Roadside Equipment |
| TIC Data Collection | "TIC Data Collection" collects transportation-related data from other centers, performs data quality checks on the collected data and then consolidates, verifies, and refines the data and makes it available in a consistent format to applications that support operational data sharing between centers and deliver traveler information to end-users. A broad range of data is collected including traffic and road conditions, transit data, emergency information and advisories, weather data, special event information, traveler services, parking, multimodal data, and toll/pricing data. It also shares data with other transportation information centers. | Transportation Information Center |
| TMC Traffic Surveillance | "TMC Traffic Surveillance" remotely monitors and controls traffic sensors and surveillance (e.g., CCTV) equipment, and collects, processes and stores the collected traffic data. Current traffic information and other real-time transportation information is also collected from other centers. The collected information is provided to traffic operations personnel and made available to other centers. | Traffic Management Center |
| Vehicle Basic Safety | "Vehicle Basic Safety" exchanges current vehicle location and motion information with other vehicles in the vicinity, uses that information to calculate vehicle paths, and warns the driver when the potential for an impending collision is detected. If available, map data is used to filter and interpret the relative location and motion of vehicles in the vicinity. Information from on-board sensors (e.g., radars and image processing) are also used, if available, in combination with the V2V communications to detect non-equipped vehicles and corroborate connected vehicle data. Vehicle location and motion broadcasts are also received by the infrastructure and used by the infrastructure to support a wide range of roadside safety and mobility applications. This object represents a broad range of implementations ranging from basic Vehicle Awareness Devices that only broadcast vehicle location and motion and provide no driver warnings to advanced integrated safety systems that may, in addition to warning the driver, provide collision warning information to support automated control functions that can support control intervention. | Vehicle OBE |
| Vehicle Border Crossing Support | "Vehicle Border Crossing Support" uses connected vehicle technology to exchange traveler credentials with border systems to support expedited clearance through international borders. | Vehicle OBE |
| Vehicle Traveler Information Reception | "Vehicle Traveler Information Reception" provides the capability for drivers to receive general transportation information including traffic and road conditions, incident information, maintenance and construction information, event information, transit information, parking information, weather information, and broadcast alerts. | Vehicle OBE |
Includes Information Flows:
| Information Flow | Description |
|---|---|
| arrival notification | Notification of arrival (and departure) of a motor vehicle at the inspection station. |
| border agency clearance results | Notification regarding the granting of permission for commercial freight shipment to enter the U.S. |
| border card data | Personal identification data from ID cards used by travelers at border crossings. |
| border clearance data | Trip specific data regarding the movement of goods across international borders. Includes trip identification number. May also include results from recent border crossing screening events. |
| border clearance data request | Request for trip specific data regarding the movement of goods across international borders. Includes trip identification number. May also include results from recent border crossing screening events. |
| border clearance event | Reports clearance event data regarding action taken at border, including acceptance or override of system decision, and date/time stamp |
| border clearance status | Notification regarding the crossing status of commercial freight shipment scheduled to enter the U.S. Includes portions of border agency and transportation agency clearance results, as they become available. |
| border crossing status information | Port of entry status including current wait-times, lane configuration and status including closures and restrictions, and notification of incidents at the border |
| border pass/pull-in | Command to commercial vehicle to pull into or bypass border inspection station |
| border security input | Information regarding security related events occurring at the border. |
| border wait times data | Measure of current, actual, or predicted wait time at border. Measurement provided by vehicle type, lane, and type of lane (e.g. NEXUS vs. regular). |
| clearance notification | Notification that cargo has been cleared through customs. |
| consolidated agency response | Electronic manifest data as well as commercial vehicle screening results. |
| container manifest | Official statement of the cargo held in a container. |
| container seal interrogation | Customs inspection of the electronic seal on a container to verify the container has not been opened or tampered with; requires proper authentication. |
| container seal status | The status of an electronic seal on a container, indicating sealing time, location, and authority, and any openings or tampering. |
| electronic lock data | Notification to roadside (via transponder) of the presence and status of electronic cargo locks. |
| electronic lock data request | Request from roadside for data regarding presence and status of electronic cargo locks. |
| inspection results | Report of results of border inspection on a particular load. |
| local border wait times | Current border wait time calculated by the RSE based on data collected from passing connected vehicles. |
| local traveler information | Traveler information including traffic, road, and weather conditions for a particular locality. This flow includes the location-specific traveler information and time effectivity of the information. |
| request tag data | Request for tag information including tag id and associated data. |
| tag data | Unique tag ID and related vehicle information. |
| transportation border clearance assessment | Includes directions for commercial driver to proceed to nearest vehicle weigh and inspection station for further review if required. |
| traveler border clearance status | Information indicating whether border clearance has been granted and instructions if additional processing is required. |
| traveler credentials | Traveler identification, including trusted traveler program information, if applicable. |
| traveler personal information | This flow includes biometric and other data to allow recognition of travelers. |
| vehicle location and motion for surveillance | Data describing the vehicle's location in three dimensions, heading, speed, acceleration, braking status, and size. This flow represents monitoring of basic safety data ('vehicle location and motion') broadcast by passing connected vehicles for use in vehicle detection and traffic monitoring applications. |
| vehicle signage data | In-vehicle signing data that augments regulatory, warning, and informational road signs and signals. The information provided would include static sign information (e.g., stop, curve warning, guide signs, service signs, and directional signs) and dynamic information (e.g., current signal states, grade crossing information, local traffic and road conditions, detours, advisories, and warnings). |
| vehicle signage local data | Information provided by adjacent field equipment to support in-vehicle signing of dynamic information that is currently being displayed to passing drivers. This includes the dynamic information (e.g., current signal states, grade crossing information, local traffic and road conditions, detours, advisories, parking availability, etc.) and control parameters that identify the desired timing, duration, and priority of the signage data. |
Application Interconnect Diagram
This is one way this application may be realized, but not the only way. There are other ways to build a given application and accomplish a stated objective.
The application interconnect diagram can be viewed in SVG or PNG format and the current format is SVG. SVG Diagram
PNG Diagram
Application Triples
Requirements
| Need | Requirement | ||
|---|---|---|---|
| N2.023 | Border Management systems need to collect transportation related data, including border crossing data to support planning and research activities that span the US land border crossings. | 2.051 | Border Management shall collect traffic conditions data from vehicles acting as probes operating near a land border crossing. |
| 2.052 | Border Management shall collect border clearance data from systems at the border to support planning and research activities, including: Number of people (passengers, drivers, and vehicle operators), Number of vehicles, and Types of Goods. | ||
| 2.053 | Border Management shall provide the collected border activities statistics data to archived data and planning systems. | ||
| N2.024 | Border Management systems need to be able to verify that people coming into the country are admissible and comply with federal laws and regulations. | 2.054 | Border Management shall collect traveler credentials information as travelers approach a land border crossing to support the determination that a traveler is in compliance with border crossing regulations. |
| 2.055 | Border Management shall notify travelers whether they are allowed to cross the border. | ||
| N2.025 | Border Management systems need to be able to verify that vehicles coming into the country are admissible and comply with federal laws and regulations. | 2.056 | Border Management shall collect vehicle credentials information as vehicles approach a land border crossing to support the determination that a vehicle is in compliance with border crossing regulations. |
| 2.057 | Border Management shall send a notification to the vehicle whether the vehicle is allowed to cross the border. | ||
| N2.026 | Border Management systems need to be able to verify that goods and cargo coming into the country are admissible and comply with federal laws and regulations. | 2.058 | Border Management shall collect credentials information of cargo or freight equipment as its conveyance (e.g. truck, chassis, or other vehicle type) approaches a land border crossing to support the determination that that cargo or freight equipment is in compliance with border crossing regulations. |
| 2.059 | Border Management shall send a notification to the conveyance (e.g. truck, chassis, other vehicle type) whether the cargo or freight equipment is allowed to cross the border. | ||
| N2.027 | Border Management systems need to be able to provide border status and wait times to travelers approaching the border crossing or planning to cross. | 2.060 | Border Management shall provide border status information to travelers approaching or planning to cross a land border crossing, including: border open/closed status, border wait times, and expedited crossing lane availability. |
| 2.061 | Border Management shall provide border status information to the traveling public using various means, including: Traveler information service providers, traffic information signs, and in-vehicle signing. | ||
| N2.028 | Border Management systems need to exchange commercial vehicle records with other agencies and stakeholders including credentials, status of the credentials, and records of fuel tax payments. | 2.062 | Border Management shall exchange commercial vehicle records with commercial vehicles , to support screening and expedited clearance at border crossings, including: credentials, credentials status, cargo manifests, tax payment reconciliation data, screening results, and inspection results. |
| N2.029 | Border Management Systems need to detect and identify the presence of hazardous materials (HAZMAT) on board commercial vehicles in order to support the quick effective response. | 2.063 | Border Management shall collect hazardous materials (HAZMAT) credentials data from vehicles and their cargo approaching a land border crossing. |
| 2.064 | Border Management shall support verification that drivers and vehicles are authorized to carry HAZMAT across the border. | ||
| 2.065 | Border Management shall collect electronic placard information as cargo or freight equipment approaches a land border crossing that indicates any and what type of hazardous materials are being carried. | ||
| N2.030 | Border Management Systems need to provide electronic communications with commercial vehicles to support security inspections and weigh-in-motion detection. | 2.066 | Border Management shall provide pass or pull-in indicators to vehicles to go into or bypass secondary inspection stations at a land border crossing. |
| N2.031 | Border Management systems need to monitor traffic flow at or near a border crossing using data from vehicles and mobile devices acting as probes to provide information to the public, adjacent traffic centers, and other border stakeholders. | 2.067 | Border Management shall collect traffic and road conditions information from vehicles acting as probes at or near a land border crossing to support border operations and incident management, including: traffic data, road weather conditions, and maintenance and construction vehicle activities. |
Related Sources
- Border Information Flow Architecture, Draft, 5/16/2012
Security
In order to participate in this application, each physical object should meet or exceed the following security levels.
| Physical Object Security | ||||
|---|---|---|---|---|
| Physical Object | Confidentiality | Integrity | Availability | Security Class |
| Border Inspection Administration Center | High | High | Moderate | Class 4 |
| Border Inspection System | High | High | High | Class 5 |
| Commercial Vehicle Administration Center | High | High | Moderate | Class 4 |
| Commercial Vehicle Check Equipment | Moderate | High | Moderate | Class 3 |
| Commercial Vehicle OBE | Moderate | Moderate | Low | Class 2 |
| Fleet and Freight Management Center | High | High | Moderate | Class 4 |
| Freight Distribution and Logistics Center | Moderate | Moderate | Moderate | Class 2 |
| Freight Equipment | Moderate | Moderate | Low | Class 2 |
| Intermodal Customer System | High | High | Moderate | Class 4 |
| Roadside Equipment | High | High | Moderate | Class 4 |
| Traffic Management Center | Not Applicable | Low | Low | Class 1 |
| Transportation Information Center | Low | Low | Low | Class 1 |
| Traveler Card | High | Moderate | High | Class 5 |
| Vehicle OBE | High | High | Moderate | Class 4 |
In order to participate in this application, each information flow triple should meet or exceed the following security levels.
| Information Flow Security | |||||
|---|---|---|---|---|---|
| Source | Destination | Information Flow | Confidentiality | Integrity | Availability |
| Basis | Basis | Basis | |||
| Border Inspection Administration Center | Border Inspection System | consolidated agency response | High | High | Moderate |
| This contains the full manifest of the cargo container, as well as the results of the vehicle screening. This data can be highly sensitive. This flow contains information about a significant number of shipments, which increases the value of this data. | This response directly determines whether or not the vehicle is cleared to cross the border. An incorrect message could lead to a vehicle which should not be allowed to cross the border ending up across the border. | The system must have an acknowledgement of a missed message. If a message is not received, it may lead to extra searches, as vehicles could not be automatically cleared. | |||
| Border Inspection Administration Center | Border Inspection System | traveler personal information | Moderate | High | Moderate |
| This flow includes PII of travelers. If it also includes the necessary challenge questions and response to impersonate that individual, it could be classified as a HIGH. | False data here could allow someone to impersonate someone else. This may lead to an unauthorized person entering the country. | The system must have an acknowledgement of a missed message. If this data is not received, the traveler will have to identify themselves through the traditional methods, such as a passport. | |||
| Border Inspection Administration Center | Fleet and Freight Management Center | clearance notification | Moderate | Low | Moderate |
| This notification is sensitive. If someone is able to know in advance that a truck was not cleared through customs, they may attempt to flee. If this contains information about the contents of a container, this could be raised to a HIGH. | This information is useful for fleet-fright managers to know, however, they will also be receiving similar information from other sources. A false message here may cause confusions, but there will be other sources of data, such as the vehicles GPS that would help clear this up. | This information is not acted upon in the Border Management System. It provides a useful service to the users, but the lack of a message would not cause the Border Management System to be harmed in any way. It is necessary for the sender to know if the message was received. | |||
| Border Inspection Administration Center | Freight Distribution and Logistics Center | clearance notification | Moderate | Low | Moderate |
| This notification is sensitive. If someone is able to know in advance that a truck was not cleared through customs, they may attempt to flee. If this contains information about the contents of a container, this could be raised to a HIGH. | This information is useful for logistic specialists to know, however, they will also be receiving similar information from other sources. A false message here may cause confusions, but there will be other sources of data, such as the vehicles GPS that would help clear this up. | This information is not acted upon in the Border Management System. It provides a useful service to the users, but the lack of a message would not cause the Border Management System to be harmed in any way. It is necessary for the sender to know if the message was received. | |||
| Border Inspection Administration Center | Intermodal Customer System | clearance notification | Moderate | Low | Moderate |
| This notification is sensitive. If someone is able to know in advance that a truck was not cleared through customs, they may attempt to flee. If this contains information about the contents of a container, this could be raised to a HIGH. | This information is useful for cargo originators or recipients to know, however, they will also be receiving similar information from other sources. | This information is not acted upon in the Border Management System. It provides a useful service to the users, but the lack of a message would not cause the Border Management System to be harmed in any way. It is necessary for the sender to know if the message was received. | |||
| Border Inspection System | Border Inspection Administration Center | border security input | Moderate | Moderate | Low |
| Since this is describing events that already occurred it is possible that someone could observe these by sitting at the border and watching. However some things in this may be slightly sensitive in nature and should not be completely visible to anyone. If this flow could carry instructions to be acted on at a later point (e.g. "Suspicious traveler, pull over down the road and investigate"), this could potentially be HIGH because it is potentially national security related information; however, it is not clear from the CVRIA description whether or not this will be the case. | This information could affect how the BIAC responds to a request on a person in the future. As such this information should be relatively secure; however mistakes in the information do not have a major impact on anything. | This information requires an acknowledgment of receipt, but if a message is missed it could be sent again at a later time without any impact on the rest of the system. | |||
| Border Inspection System | Border Inspection Administration Center | inspection results | Moderate | Moderate | Low |
| This information should be protected as much as possible, however the disclosure of this information will not have a significant impact on those involved. | This information could affect how the BIAC responds to a request on a person in the future. As such this information should be relatively secure; however mistakes in the information do not have a major impact on anything. | This information requires an acknowledgment of receipt, but if a message is missed it could be sent again at a later time without any impact on the rest of the system. | |||
| Border Inspection System | Commercial Vehicle Administration Center | arrival notification | Low | Moderate | Low |
| This information can be directly observed at the border. | This information could affect how the CVAC responds to a request on a vehicle in the future. As such this information should be relatively secure; however mistakes in the information do not have a major impact on anything. | This information requires an acknowledgment of receipt, but if a message is missed it could be sent again at a later time without any impact on the rest of the system. | |||
| Border Inspection System | Commercial Vehicle Check Equipment | inspection results | Moderate | Low | Low |
| This could contain information on what is in a particular load. As such it could be used by a malicious individual to determine which vehicles are a greater target then the rest. | This is an informational message and as such any errors in it should not affect anything. If this has higher integrity though then it will be more likely to be useful. | This information requires an acknowledgment of receipt, but if a message is missed it could be sent again at a later time without any impact on the rest of the system. | |||
| Border Inspection System | Roadside Equipment | border pass/pull-in | Not Applicable | High | Moderate |
| This is directly observable data. | This message is directly acted upon. It should not be possible to spoof a border inspection station bypass. | The system should know if these messages are not received. If the messages are not received, the system should fail safely, with the border agents performing additional inspections. | |||
| Border Inspection System | Roadside Equipment | clearance notification | Low | High | Moderate |
| This is directly observable data. | This message is directly acted upon. It should not be possible to spoof a border inspection station bypass. | The system should know if these messages are not received. If the messages are not received, the system should fail safely, with the border agents performing additional inspections. | |||
| Border Inspection System | Roadside Equipment | traveler border clearance status | Low | High | Moderate |
| This is directly observable data. | This message is directly acted upon. It should not be possible to spoof a border inspection station bypass. | The system should know if these messages are not received. If the messages are not received, the system should fail safely, with the border agents performing additional inspections. | |||
| Border Inspection System | Roadside Equipment | vehicle signage local data | Not Applicable | Moderate | Moderate |
| This data is intentionally transmitted to everyone via a broadcast. It is meant to augment other signage data, and by definition is meant to be shared with everyone. | These signs are meant to augment other visual cues to the driver. They should be accurate, but any inaccuracies should be corrected for by other means. | These notifications are helpful to a driver, but if the driver does not receive this notification immediately, there should still be other visual cues. | |||
| Border Inspection System | Traffic Management Center | border wait times data | Not Applicable | Low | Low |
| This is directly observable data. | If this information is used to determine how thoroughly to investigate passing vehicles (ie. When it is busy vehicles are subject to less thorough inspection) this flow could be bumped up to a MEDIUM. | If this information is not fully up to date, or is missing, the system can still operate properly. | |||
| Border Inspection System | Transportation Information Center | border crossing status information | Low | Low | Low |
| This is all public information which is mostly available through public information channels. | A flaw in this information will not cause much, if any harm. A higher integrity will allow this information to be of more use, but is not required for security reasons. | Without this information there will not be any direct problem. A higher availability will allow this information to be more useful; however it is not a requirement. | |||
| Commercial Vehicle Administration Center | Border Inspection Administration Center | border clearance status | High | High | Moderate |
| This includes information regarding what is being shipped across the border, which contains highly sensitive information. This also includes data regarding clearance results, which is also sensitive. This flow contains information about a significant number of shipments, which increases the value of this data. | This information is used later in the decision process. Future trips across the border take past data into account. Incorrect data here may lead to incorrect decisions made regarding letting something across the border. | This is all recent data, it is not acted upon immediately. This system should operate correctly with a few missed messages. It is necessary for the sender to know if the message was received. | |||
| Commercial Vehicle Administration Center | Commercial Vehicle Check Equipment | border agency clearance results | Low | High | Moderate |
| This information is observable by seeing if the freight shipment enters the U.S. It should only contain the result of the analysis, and should not contain sensitive information. | If this message is incorrect or altered, it could have a significant economic impact. This message is one requirement to determine if a freight shipment is allowed to enter the U.S. | This message is used to determine whether or not a freight shipment can cross the border. If this message is not received, the recipient must be aware, so that they can request the result again. A slightly delay will not have a significant impact on the border crossing. | |||
| Commercial Vehicle Administration Center | Commercial Vehicle Check Equipment | transportation border clearance assessment | Moderate | High | Moderate |
| In general, the result of this assessment will be clearly indicated by a vehicle being allowed through, or told to stop. However, if a vehicle that will be stopped is able to learn about it in advance, they could attempt to flee. | An incorrect message indicating to check a vehicle that doesn't need to be checked would simply lead to wasted unnecessary inspections, however, an incorrect message claiming that a vehicle does not need an inspection could lead to a vehicle containing contraband not being inspected. | The system must have an acknowledgement of a missed message. If a message is not received, it may lead to extra searches, as vehicles could not be automatically cleared. | |||
| Commercial Vehicle Administration Center | Fleet and Freight Management Center | border clearance status | High | Low | Moderate |
| This includes information regarding what is being shipped across the border, which contains highly sensitive information. This also includes data regarding clearance results, which is also sensitive. This flow contains information about a significant number of shipments, which increases the value of this data. | This information is useful for fleet-fright managers to know, however, they will also be receiving similar information from other sources. A false message here may cause confusion, but there will be other sources of data, such as the vehicles GPS that would help clear this up. | This information is not acted upon in the Border Management System. It provides a useful service to the users, but the lack of a message would not cause the Border Management System to be harmed in any way. It is necessary for the sender to know if the message was received. | |||
| Commercial Vehicle Administration Center | Intermodal Customer System | border clearance status | High | Low | Moderate |
| This includes information regarding what is being shipped across the border, which contains highly sensitive information. This also includes data regarding clearance results, which is also sensitive. This flow contains information about a significant number of shipments, which increases the value of this data. | This information is useful for cargo originators or recipients to know, however, they will also be receiving similar information from other sources. | This information is not acted upon in the Border Management System. It provides a useful service to the users, but the lack of a message would not cause the Border Management System to be harmed in any way. It is necessary for the sender to know if the message was received. | |||
| Commercial Vehicle Check Equipment | Commercial Vehicle Administration Center | border clearance event | Moderate | Moderate | Moderate |
| This data could be sensitive in nature, and should be protected as such. | This data is not directly effecting any decisions made in the system. It may be used in an aggregate to influence future decisions, but any inaccuracies should not have a significant affect. | The system must have an acknowledgement of a missed message. It is not acted upon in real time, but the CVAC should receive all records at some point. | |||
| Commercial Vehicle Check Equipment | Roadside Equipment | border pass/pull-in | Not Applicable | High | Moderate |
| This is directly observable data. | This message is directly acted upon. It should not be possible to spoof a border inspection station bypass. | The system should know if these messages are not received. If the messages are not received, the system should fail safely, with the border agents performing additional inspections. | |||
| Commercial Vehicle OBE | Roadside Equipment | border clearance data | Moderate | Moderate | Low |
| This is a broadcast message so any sensitive information about the trip should be kept out of the message. | This data is being reported by the vehicles attempting to cross the border, all the data reported by them should be verified before being trusted. Considering that, the integrity could never be a HIGH. However if this data is incorrect often, it will be of little use to the system. | If this data is missing, the system cannot make a decision about how to handle that vehicle. However, there are multiple chances for this data to be transmitted and received. Additionally, if the vehicle is not pre-approved it will be handled by border security. | |||
| Commercial Vehicle OBE | Roadside Equipment | electronic lock data | Low | Moderate | Low |
| The presence of electronic locks will most likely be observable by looking at the cargo doors. | This data is being reported by the vehicles attempting to cross the border, all the data reported by them should be verified before being trusted. Considering that, the integrity could never be a HIGH. However if this data is incorrect often, it will be of little use to the system. | If this data is missing, the system cannot make a decision about how to handle that vehicle. However, there are multiple chances for this data to be transmitted and received. Additionally, if the vehicle is not pre-approved it will be handled by border security. | |||
| Commercial Vehicle OBE | Roadside Equipment | tag data | Low | Moderate | Low |
| This is broadcast data. | False data here could lead to a misclassification of the vehicle. If it was an accidental error, it would be easy to correct. | . If this data is missing, the system cannot make a decision about how to handle that vehicle. However, there are multiple chances for this data to be transmitted and received. Additionally, if the vehicle is not pre-approved it will be handled by border security. | |||
| Freight Equipment | Roadside Equipment | container manifest | Moderate | Moderate | Low |
| The contents of a freight container may not necessarily be something that should be made public. If it is known that a container is carrying high value objects, it may be the target of theft. | Due to the nature of this information, it is impossible to be certain that what it states is true, thus it cannot have a HIGH integrity. However, it should be as accurate as possible. | If this data is missing, the system cannot make a decision about how to handle that vehicle. However, there are multiple chances for this data to be transmitted and received. Additionally, if the vehicle is not pre-approved it will be handled by border security. | |||
| Freight Equipment | Roadside Equipment | container seal status | Low | Moderate | Low |
| The presence of electronic locks will most likely be observable by looking at the cargo doors and the other information is not sensitive in nature. | This data is being reported by the containers attempting to cross the border, all the data reported by them should be verified before being trusted. Considering that, the integrity could never be a HIGH. However if this data is incorrect often, it will be of little use to the system. | If this data is missing, the system cannot make a decision about how to handle that vehicle. However, there are multiple chances for this data to be transmitted and received. Additionally, if the vehicle is not pre-approved it will be handled by border security. | |||
| Freight Equipment | Roadside Equipment | tag data | Low | Moderate | Low |
| This data is not sensitive. | False data here could lead to a misclassification of the vehicle. If it was an accidental error, it would be easy to correct. | If this data is missing, the system cannot make a decision about how to handle that vehicle. However, there are multiple chances for this data to be transmitted and received. Additionally, if the vehicle is not pre-approved it will be handled by border security. | |||
| Roadside Equipment | Border Inspection System | container manifest | Moderate | Moderate | Low |
| The contents of a freight container may not necessarily be something that should be made public. If it is known that a container is carrying high value objects, it may be the target of theft. | Due to the nature of this information, it is impossible to be certain that what it states is true, thus it cannot have a HIGH integrity. However, it should be as accurate as possible. | If the vehicle is not pre-approved it will be handled by border security. Therefore, it is not clear that there is any security risk from failures of availability; more availability allows the operator to benefit from the processing efficiency gains associated with this application but any level of availability is acceptable from a security point of view. | |||
| Roadside Equipment | Border Inspection System | container seal status | Moderate | Moderate | Low |
| Knowing which containers are sealed and not as likely to be checked could be useful to a malicious individual. However there will not be much time for said malicious individuals to actually take advantage of the information. | Due to the nature of this information, it is impossible to be certain that what it states is true, thus it cannot have a HIGH integrity. However, it should be as accurate as possible. | If the vehicle is not pre-approved it will be handled by border security. Therefore, it is not clear that there is any security risk from failures of availability; more availability allows the operator to benefit from the processing efficiency gains associated with this application but any level of availability is acceptable from a security point of view. | |||
| Roadside Equipment | Border Inspection System | local border wait times | Not Applicable | Low | Low |
| This is directly observable data. | If this information is used to determine how thoroughly to investigate passing vehicles (ie. When it is busy vehicles are subject to less thorough inspection) this flow could be bumped up to a MEDIUM. | If this information is not fully up to date, or is missing, the system can still operate properly. | |||
| Roadside Equipment | Border Inspection System | tag data | Low | Moderate | Low |
| This is broadcast data. | This needs to verify that it is coming from a valid sender. | If this request is not received, the system will not broadcast its tag data. However, there are multiple chances for this data to be transmitted and received. Additionally, if the vehicle is not pre-approved it will be handled by border security. | |||
| Roadside Equipment | Border Inspection System | traveler credentials | High | Moderate | Moderate |
| This contains sensitive information on multiple individuals that could potentially be used to impersonate them or steal their identity. If anyone other than the intended parties can view this information it could lead to a large financial cost for many individuals. | The identity reported by this transmission might not actually be the individual in the vehicle. This categorization assumes that this information is the information from the OBE->RSE flow of the same name, forwarded by the RSE; if a border officer can add information at the RSE that gets sent to the BIS, then the integrity requirement could potentially be raised to HIGH as this flow might be used to make law enforcement decisions involving the use of force. We assume that if this information is added it is added at the BIS rather than the RSE, so this integrity requirement on this flow is MEDIUM. | Assuming it is still possible to validate travelers in the way that is currently possible this is acceptable as a MEDIUM. If when this system is down, the border cannot process any individuals then this would need to be a HIGH because completely shutting down the border could cause significant financial problems. | |||
| Roadside Equipment | Commercial Vehicle Check Equipment | border clearance data | Low | High | Low |
| This is a retransmission of low confidential data. | False data here could lead to a misclassification of the vehicle. If this data were forged, it could be used to allow an unauthorized shipment across the border | If this data is missing, the system cannot make a decision about how to handle that vehicle. However, there are multiple chances for this data to be transmitted and received. Additionally, if the vehicle is not pre-approved it will be handled by border security. | |||
| Roadside Equipment | Commercial Vehicle Check Equipment | electronic lock data | Low | Moderate | Low |
| This is a retransmission of low confidential data. | No matter what the lock state is, there is no way to guarantee that exactly the right contents were put in the container before the lock was locked. Therefore, unless there is a HIGH-integrity process for inspecting the contents of each container, there is no value in providing HIGH integrity data about the state of the lock. This suggests that a MEDIUM integrity information flow is sufficient for the correct operation of this application. Note however that if a HIGH-integrity process is available for inspecting the contents of a particular container, then having HIGH integrity on this information flow might be valuable as it might allow the container to be processed more rapidly at the border crossing than would be the case for a MEDIUM-integrity information flow. So individual participants may choose to invest in a HIGH-integrity system, but the baseline requirement is MEDIUM integrity. | If this data is missing, the system cannot make a decision about how to handle that vehicle. However, there are multiple chances for this data to be transmitted and received. Additionally, if the vehicle is not pre-approved it will be handled by border security. | |||
| Roadside Equipment | Commercial Vehicle Check Equipment | tag data | Low | Moderate | Low |
| This is a retransmission of low confidential data | False data here could lead to a misclassification of the vehicle. If this data were forged, it could be used to allow an unauthorized shipment across the border. | If this data is missing, the system cannot make a decision about how to handle that vehicle. However, there are multiple chances for this data to be transmitted and received. Additionally, if the vehicle is not pre-approved it will be handled by border security. | |||
| Roadside Equipment | Commercial Vehicle OBE | border clearance data request | Not Applicable | Moderate | Low |
| This request is sent to all vehicles entering the border, and does not contain any sensitive information. | This needs to verify that it is coming from a valid sender. | If this request is not received, the system will not broadcast its tag data. However, there are multiple chances for this data to be transmitted and received. Additionally, if the vehicle is not pre-approved it will be handled by border security. | |||
| Roadside Equipment | Commercial Vehicle OBE | border clearance event | Not Applicable | Low | Low |
| This is directly observable data. | If this is ever wrong, border agents should be able to notice and correct the issue. As such this flow is useful, but alterations to the data, either through malicious means or random problems, should not affect the overall application or its users significantly. | If this this information is not received the CV OBE will not know how to proceed, however border agents should be able to resolve this issue. | |||
| Roadside Equipment | Commercial Vehicle OBE | border pass/pull-in | Not Applicable | High | Low |
| This is directly observable data | This message is directly acted upon. It should not be possible to spoof a border inspection station bypass. | If a vehicle does not receive this data, they will be forced to stop and communicate with a border guard. This may cause a slight delay. However, it will not have a significant impact. | |||
| Roadside Equipment | Commercial Vehicle OBE | clearance notification | Not Applicable | Moderate | Low |
| This is directly observable data | If a vehicle is cleared to go through, but ends up stopping, it is an easily correctable mistake that will only cause a slight delay. On the other hand, if a vehicle that was supposed to stop does not receive the stop notification, they may attempt to travel across the border without knowing they were supposed to stop. If there is no way for border guards to easily inform the driver to stop, this could be raised to a HIGH. | If a vehicle does not receive this data, they will be forced to stop and communicate with a border guard. This may cause a slight delay. However, it will not have a significant impact. | |||
| Roadside Equipment | Commercial Vehicle OBE | electronic lock data request | Low | Moderate | Low |
| This request is sent to all vehicles entering the border, and does not contain any sensitive information. | This needs to verify that it is coming from a valid sender. | If this request is not received, the system will not broadcast its Electronic Lock Data. However, there are multiple chances for this data to be transmitted and received. Additionally, if this information is never received the vehicle will be handled in the same way that it was prior to the implementation of this system. | |||
| Roadside Equipment | Commercial Vehicle OBE | request tag data | Low | Moderate | Low |
| This request is sent to all vehicles entering the border, and does not contain any sensitive information. | This needs to verify that it is coming from a valid sender. | If this request is not received, the system will not broadcast its tag data. However, there are multiple chances for this data to be transmitted and received. Additionally, if the vehicle is not pre-approved it will be handled by border security. | |||
| Roadside Equipment | Freight Equipment | container seal interrogation | Low | Moderate | Low |
| The presence of electronic locks will most likely be observable by looking at the cargo doors and the other information is not sensitive in nature. | The container seal status returned after this interrogation will not have a HIGH integrity, as such is interrogation does not require a HIGH integrity. If the integrity of the container seal status is somehow possible to raise to a HIGH, then this could also have a HIGH integrity. | If this interrogation is not received, the system will not broadcast its Container Seal Status. However, there are multiple chances for this data to be transmitted and received. Additionally, if this information is never received the vehicle will be handled in the same way that it was prior to the implementation of this system. | |||
| Roadside Equipment | Traffic Management Center | local border wait times | Not Applicable | Moderate | Low |
| This is directly observable data | If this information is used to determine how thoroughly to investigate passing vehicles (ie. When it is busy vehicles are subject to less thorough inspection) this flow could be bumped up to a MEDIUM. | If this information is not fully up to date, or is missing, the system can still operate properly. | |||
| Roadside Equipment | Vehicle OBE | local traveler information | Not Applicable | Low | Low |
| This data is intentionally transmitted to everyone via a broadcast. It can also be determined via other visual indicators. | Flaws in this information will have a minimal effect on systems receiving it. All of the information can be verified through other means, and in a worst case scenario will only cause slightly increased traffic in the general proximity of the RSE. | All of the information provided through this flow will be available from other sources and no systems will directly rely upon it. | |||
| Roadside Equipment | Vehicle OBE | traveler border clearance status | Not Applicable | Moderate | Moderate |
| This is directly observable data | If a vehicle is cleared to go through, but ends up stopping, it is an easily correctable mistake that will only cause a slight delay. On the other hand, if a vehicle that was supposed to stop does not receive the stop notification, they may attempt to travel across the border without knowing they were supposed to stop. If there is no way for border guards to easily inform the driver to stop, this could be raised to a HIGH. | If a vehicle does not receive this data, they will be forced to stop and communicate with a border guard. This may cause a slight delay. However, it will not have a significant impact. | |||
| Roadside Equipment | Vehicle OBE | vehicle signage data | Not Applicable | Moderate | Moderate |
| This data is intentionally transmitted to everyone via a broadcast. It is meant to augment other signage data, and by definition is meant to be shared with everyone. | These signs are meant to augment other visual cues to the driver. They should be accurate, but any inaccuracies should be corrected for by other means. | These notifications are helpful to a driver, but if the driver does not receive this notification immediately, there should still be other visual cues. | |||
| Traveler Card | Border Inspection System | border card data | High | Moderate | High |
| This data contains all of the information needed to identify a traveler. If a criminal was able to view this data, it could be used to impersonate the traveler. | The identity reported by this transmission might not actually be the individual in the vehicle. As such there is no way that this could have HIGH integrity, and is why other sources must be used to ensure that this individual is who they are claiming to be. | If the traveler card data was not delivered to the RSE by Vehicle OBE this will be the last chance for the card to be validated. If it fails, the traveler will likely be turned away from the border and not be allowed to cross. This would be equivalent to arriving at the border today without a passport, however it would be the system's fault, not the user's. Since there is no alternate way for an individual to prove their identity, this could break the whole system and should not happen. | |||
| Traveler Card | Vehicle OBE | border card data | High | Moderate | Low |
| This data contains all of the information needed to identify a traveler. If a criminal was able to view this data, it could be used to impersonate the traveler. | The identity reported by this transmission might not actually be the individual in the vehicle. As such there is no way that this could have HIGH integrity, and is why other sources must be used to ensure that this individual is who they are claiming to be. | If this data is missing, the vehicle will not be able to transmit the data to RSEs. However, there are multiple chances for this data to be transmitted and received. Additionally, if the vehicle is not pre-approved it will be handled by border security. | |||
| Vehicle OBE | Roadside Equipment | traveler credentials | High | Moderate | Low |
| This data contains all of the information needed to identify a traveler. If a criminal was able to view this data, it could be used to impersonate the traveler. | The identity reported by this transmission might not actually be the individual in the vehicle. As such there is no way that this could have HIGH integrity, and is why other sources must be used to ensure that this individual is who they are claiming to be. | If this data is missing, the system cannot make a decision about how to handle that vehicle. However, there are multiple chances for this data to be transmitted and received. Additionally, if the vehicle is not pre-approved it will be handled by border security. | |||
| Vehicle OBE | Roadside Equipment | vehicle location and motion for surveillance | Not Applicable | Moderate | Moderate |
| This is directly observable data | Incorrect information here could lead to the system not functioning properly. If they are unable to properly detect all vehicles crossing the border, it would lead to confusion. There are other factors, such as visual indicators, of vehicles crossing the border, which can be used to help mitigate contradicting information. | This information must be available in a timely manner for the system to act upon it. The system can operate correctly if some messages are missed, but overall a majority of them should be received. | |||