Link Type: Center to Center
Authorizing Center --> Other Authorizing Centers:
permission request coordination
This triple is bi-directional. See also
Other Authorizing Centers --> Authorizing Center: permission request coordination
Definitions
permission request coordination (Information Flow): Coordination of permission requests between jurisdictions or regions that allow permissions to be managed that may span more than one jurisdiction.
Authorizing Center (Source Physical Object): The 'Authorizing Center' provides the functionality needed to enable data exchange between and among mobile and fixed transportation users. Its primary mission is to enable safety, mobility and environmental communications-based applications for both mobile and non-mobile users. The Authorizing Center has some jurisdiction over limited access resources; typically this includes roadside application access and radio spectrum licensing. It may be implemented as an autonomous center or as a set of supporting services that are co-located within another center.
Other Authorizing Centers (Destination Physical Object): 'Other Authorizing Centers' provides a source and destination for information flows between multiple authorizing centers that manage permissions for the Connected Vehicle Environment. The interface represented by this object enables coordination of permissions between centers in different regions, jurisdictions, or application areas.
Included In
This Information Flow is in the following Applications:
This Information Flow is in the following Application Objects:
Communication Diagrams
The communication diagram(s) can be viewed in SVG or PNG format and the current format is SVG. Switch to PNG format.
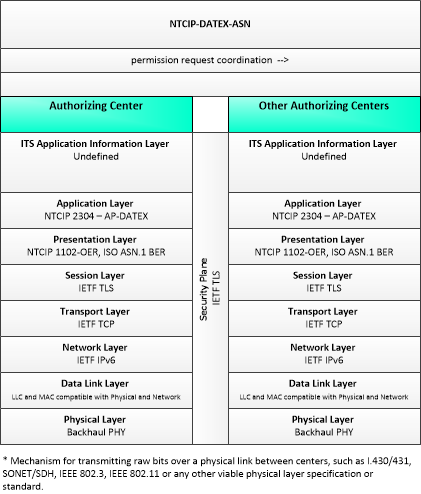
This profile describes an alternative set of standards applicable to communications between entities using ISO TC204 WG9 DATa Exchange(DATEX). Information messages are encoded using the NTCIP Octet Encoding Rules (OER).
Characteristics
Architectural:
| Characteristic | Value |
|---|---|
| Time Context | Static |
| Spatial Context | Regional |
| Acknowledgement | True |
| Cardinality | Unicast |
| Initiator | Destination |
Security
This information flow triple is in the following applications with the following security levels.
| Information Flow Security | |||||
|---|---|---|---|---|---|
| Application | Confidentiality | Integrity | Availability | ||
| Basis | Basis | Basis | |||
| Security levels have not been defined yet. | |||||