Link Type: Center to Center
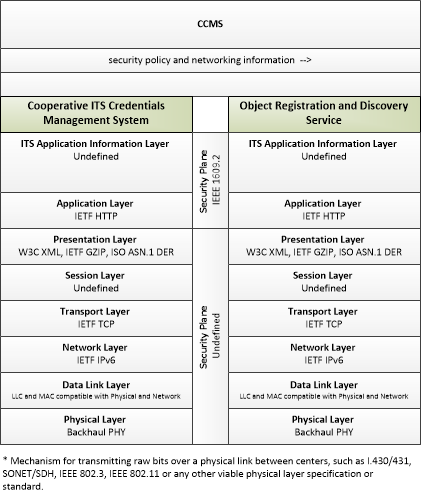
Cooperative ITS Credentials Management System --> Object Registration and Discovery Service:
security policy and networking information
Definitions
security policy and networking information (Information Flow): Security policy information describing the CCMS' enrollment, authorization, misbehavior and revocation policies, and communications information related to CCMS components; including contact information and public credentials of those components.
Cooperative ITS Credentials Management System (Source Physical Object): The 'Cooperative ITS Credentials Management System' (CCMS) is a high-level aggregate representation of the interconnected systems that enable trusted communications between mobile devices and other mobile devices, roadside devices, and centers and protect data they handle from unauthorized access. Representing the different interconnected systems that make up a Public Key Infrastructure (PKI), this physical object represents an end user view of the credentials management system with focus on the exchanges between the CCMS and user devices that support the secure distribution, use, and revocation of trust credentials.
Object Registration and Discovery Service (Destination Physical Object): The 'Object Registration and Discovery Service' represents one or more center-based applications that provide registration and lookup services necessary to allow objects to locate (for communications purposes) other objects operating within the Connected Vehicle Environment. These registration and discovery services are support services that enable other applications.
Included In
This Information Flow is in the following Applications:
This Information Flow is in the following Application Objects:
Communication Diagrams
The communication diagram(s) can be viewed in SVG or PNG format and the current format is SVG. Switch to PNG format.
Characteristics
Architectural:
| Characteristic | Value |
|---|---|
| Time Context | Recent |
| Spatial Context | National |
| Acknowledgement | True |
| Cardinality | Unicast |
| Initiator | Destination |
Security
This information flow triple is in the following applications with the following security levels.
| Information Flow Security | |||||
|---|---|---|---|---|---|
| Application | Confidentiality | Integrity | Availability | ||
| Basis | Basis | Basis | |||
| Security levels have not been defined yet. | |||||